“Maltrail“ is an open-source malicious traffic detection system that utilizes publicly available spam lists and blacklists of suspicious trails. It also employs static trails from various antivirus reports and custom user-defined lists. This system identifies malicious domains, URLs of known malicious executables, and IP addresses of known attackers as trails. Additionally, Maltrail employs advanced heuristic mechanisms to discover unknown threats, such as new malware. You can find the project on GitHub at: https://github.com/stamparm/maltrail/
The GitHub page provides resources for blacklists (i.e., feeds), static entries, and trails of various malware command and control centers or sinkholes used in this detection system.
Deployment Architecture
According to the project’s website, Maltrail is based on a Traffic–> Sensor <-> Server <-> Client architecture.
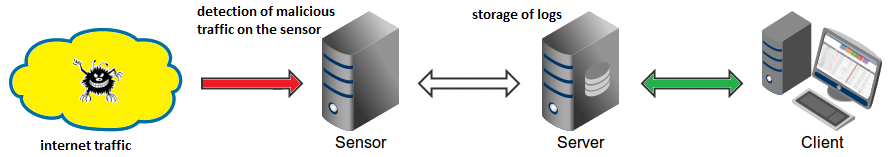
Sensors are standalone components running on a Linux platform, passively connected to a SPAN/mirrored port or transparently inline on a Linux bridge. They monitor the passing traffic for blacklisted items, such as domain names, URLs, and IPs. If a match is found, event details are sent to the central server and stored in the appropriate logging directory. When the Sensor and Server are on the same machine (default configuration), logs are stored locally. All events for the selected 24-hour period are sent to the Client, a reporting web application, responsible for presenting the events.
Prerequisites
In this guide, Maltrail will be installed on an Ubuntu 18.04 LTS virtual machine (VM). To properly execute Maltrail, Python 2.7 is required, alongside the pcapy package. The only other requirement is for the Sensor and Server components to run with root privileges. Use the following command to install the python-pcapy package and its dependencies:
apt-get install git python-pcapy
Running Maltrail System
Download the latest package with the following command, then run the Python scripts for the server and sensor in the terminal:
git clone https://github.com/stamparm/maltrail.git
cd maltrail/
Start Maltrail Sensor
Start the sensor in the terminal with the following command:
python sensor.py
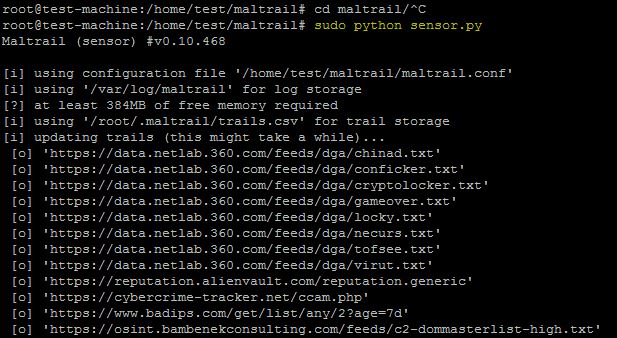
If the Maltrail list isn’t updated, it will be while running the sensor.
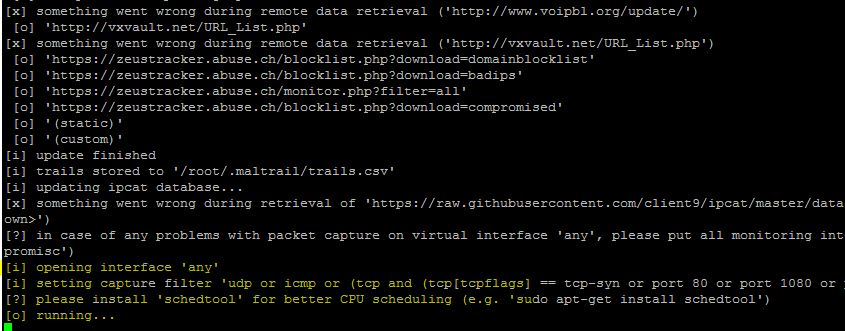
The sensor is successfully running on the machine, as shown above.
Start Maltrail Server
To start the server on the same machine, open a new terminal and execute the following commands:
cd maltrail
python server.py
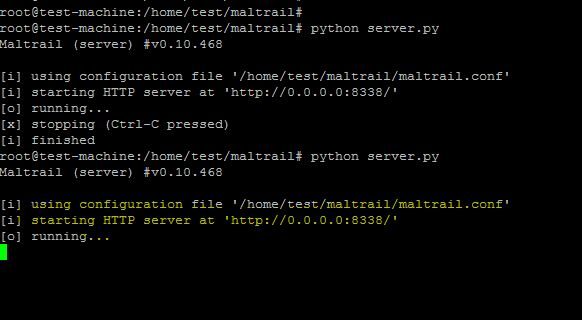
The HTTP server is running on port 8338, as seen in the snapshot above. Ensure this port is allowed through the firewall if accessing the web interface behind it.
Maltrail Dashboard
Access the reporting interface by visiting http://localhost:8338 (default credentials are admin:changeme!, saved in the maltrail.conf file) from your web browser. You will see the following authentication window—enter the credentials to access the Maltrail web portal.
Once inside, admins will be presented with the reporting interface.
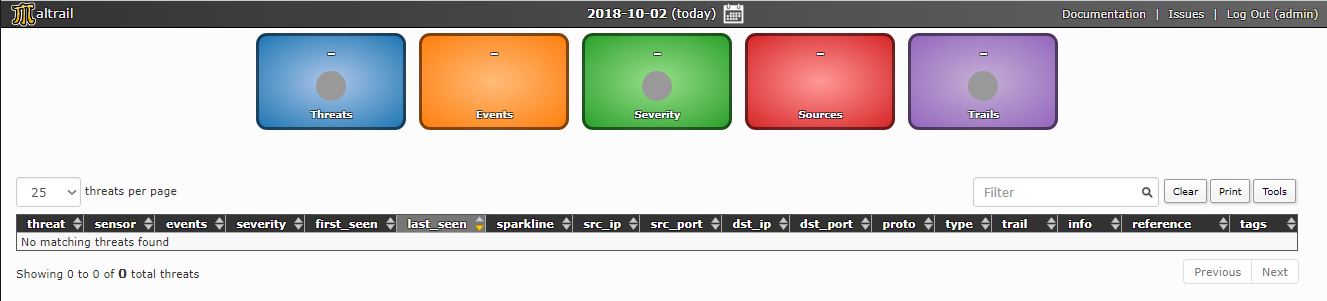
Testing Maltrail
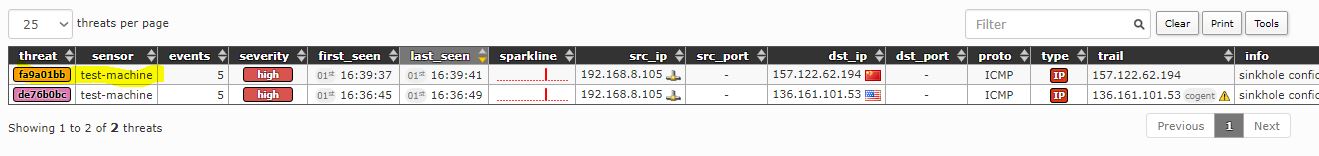
The project site suggests using this test: IP address “136.161.101.53” is a malicious address, and Maltrail will detect and show it on the Dashboard:
ping -c 5 136.161.101.53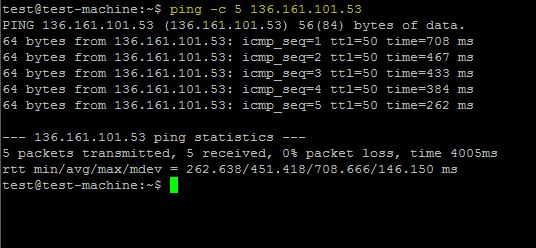
cat /var/log/maltrail/02-10-2018.log
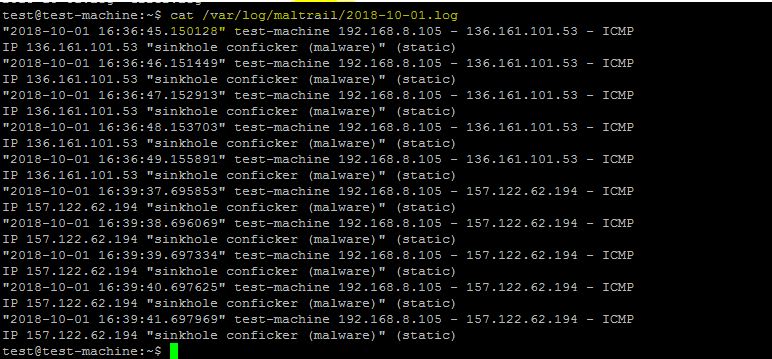
Both attacks (pings to a malicious IP) are also shown in the frontend, as depicted below.
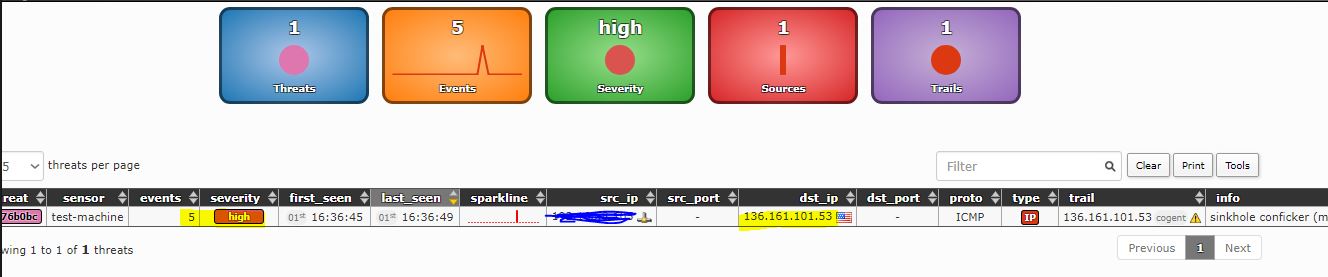
—————————————————————————————
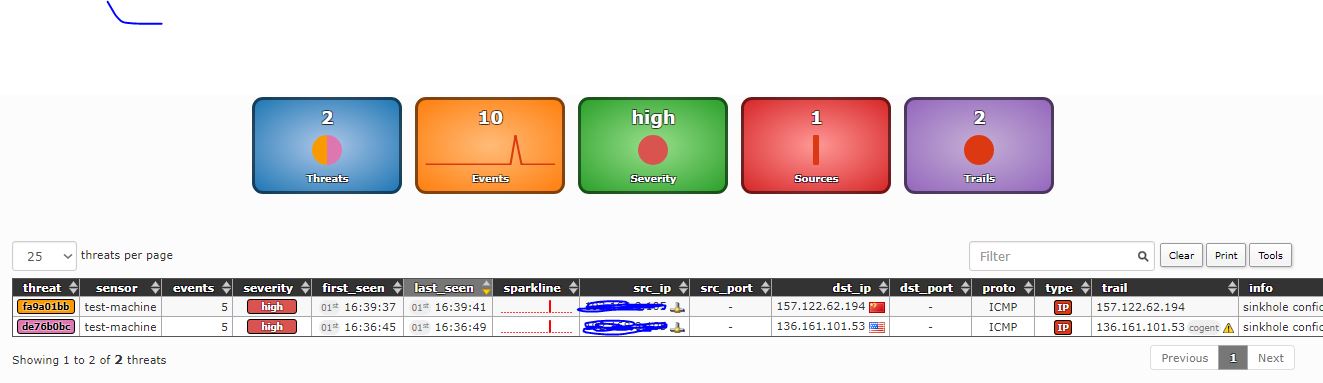
The top part of the frontend includes a sliding timeline that activates when clicked. The middle section summarizes displayed events. The “Events” box represents total events over a 24-hour period, color-coded by event type (IP-based, DNS-based, URL-based). Click boxes for detailed graphs.

The bottom part of the frontend offers a condensed view of logged events in a paginated table.
Configuration of Maltrail Sensor/Server
The configuration for the Maltrail sensor is found in the maltrail.conf file under the [Sensor] section, with parameters explained via comments. Users can set options like static feed update period and network interface settings.
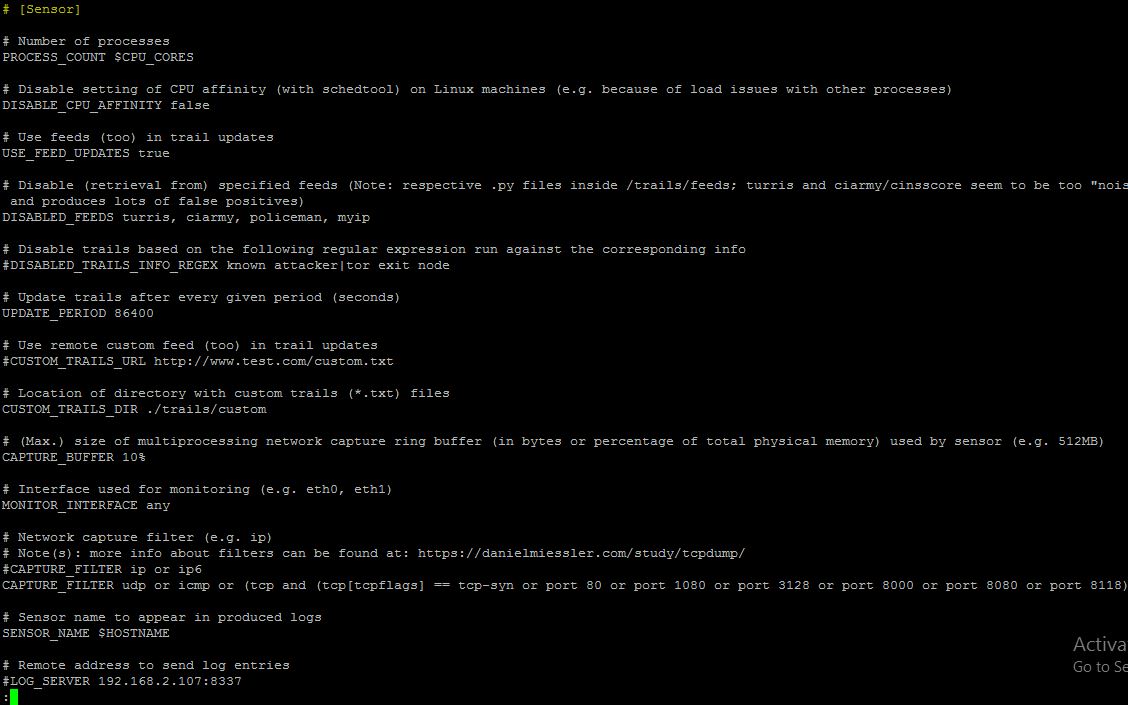
sensor section
————————————————————————————–
In the server section, users can specify the listening port and IP address, and enable SSL to secure web traffic.
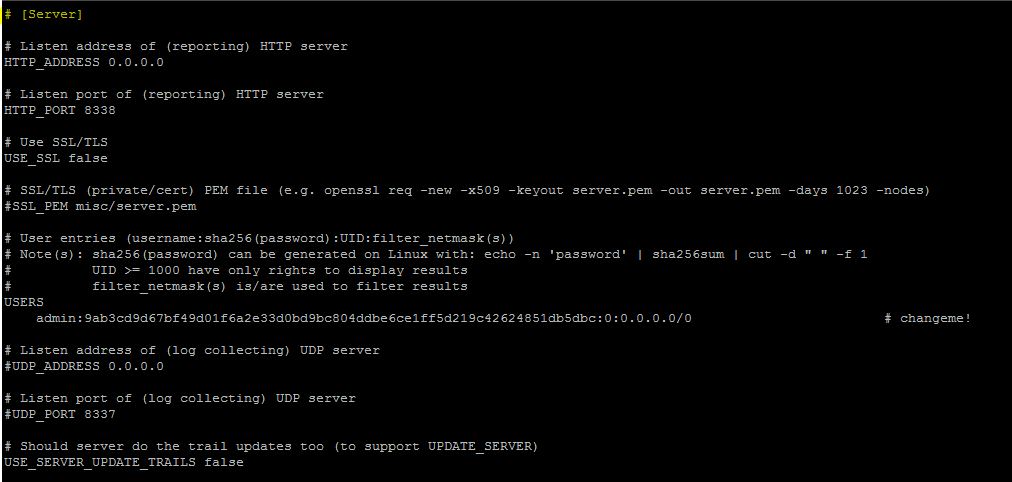
server section
Log Storage
Maltrail logs detected events in the server’s defined logging directory, the path set by the LOG_DIR option in maltrail.conf. Events are stored by date.
Port Sweep
Maltrail detects excessive connection attempts to certain TCP ports, warning of potential port scanning through heuristic mechanisms.
False Positives
Like other security solutions, Maltrail may report “false positives.” These occur when regular user behavior is mistakenly marked as suspicious or malicious. For example, legitimate Google IPs might be flagged from repeated domain/IP scanning.
Conclusion
This guide covers Maltrail, a malicious traffic detection system that identifies threats via static feeds and heuristic mechanisms. Developed in Python, Maltrail’s sensor and server components can run on one machine to monitor traffic on any interface, offering network security against known internet threats. Although limited to detection, it may integrate with other tools for IP blocking via iptables.
FAQ
What is Maltrail?
Maltrail is an open-source system that detects malicious traffic using blacklists and heuristic methods.
Which platforms support Maltrail?
Maltrail is designed to run on Linux platforms.
What are the prerequisites for installing Maltrail?
You’ll need Python 2.7 and the pcapy package to run Maltrail. Root privileges are required for the Sensor and Server components.
Can Maltrail block malicious traffic?
Currently, Maltrail is a detection-based system. However, it can be integrated with other tools for traffic blocking.
