An Identity and Access Management (IAM) service is offered by many cloud providers to regulate access to cloud resources. This ensures that only authenticated and authorized users can access these resources. In AWS, IAM consists of users, groups, and roles. This guide will focus on IAM roles.
Overview
IAM roles are similar to users in that IAM policies can be attached to both, defining the permissions available. However, unlike IAM users who have long-term credentials, roles provide temporary security credentials. These roles can be assumed by applications, services, or users that require access to AWS resources.
Objectives
In this tutorial, you’ll learn to use the ‘IAM PassRole’ permission. We will demonstrate how to connect an EC2 instance to a private S3 bucket using this permission.
Understanding PassRole Permission
When setting up AWS services, passing a role to the service is often required. The service assumes the role to perform authorized actions. This setup is typically done once during service configuration. PassRole is a security feature allowing specific users to delegate role permissions to AWS services.
PassRole Permission Demonstration
Let’s delve into this topic using a practical example. We will configure a role allowing an EC2 instance to access an S3 bucket. Our application will have temporary credentials to authenticate and interact with S3.
The EC2 instance is asked to select an IAM role during launch, which provides these credentials. To enable this, follow three key steps:
- Create and attach a policy to define the IAM role’s permission scope.
- Associate a trust policy with the role for EC2 to assume it.
- Attach an IAM permission policy to the user, allowing role passing.
Creating the Role
We will create a role ‘EC2S3Access’ with ‘AmazonS3ReadOnlyAccess’ policy:
Step 1. Navigate to the IAM dashboard and select ‘Roles,’ then click ‘Create Role.’
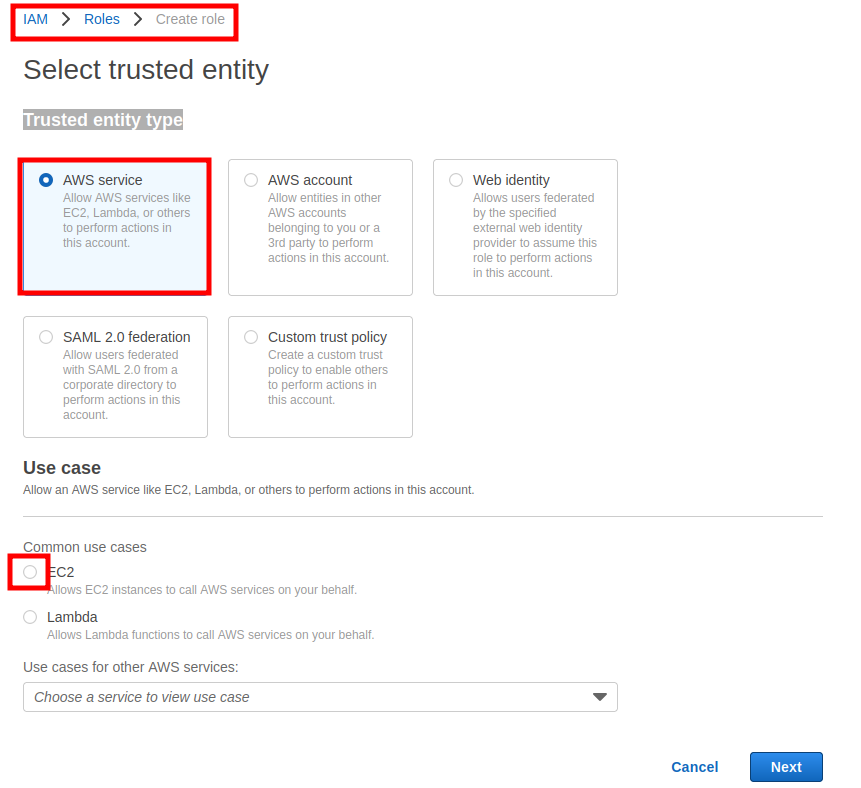
Step 2. Under ‘Select trusted entity,’ choose ‘AWS service’ and for the ‘Use case’ select ‘EC2.’
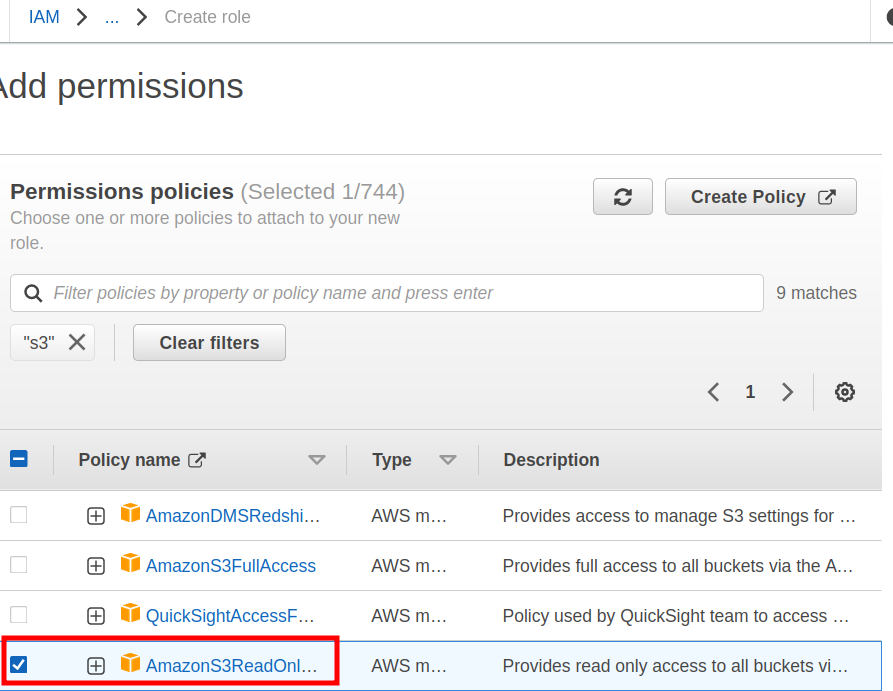
Step 3. In ‘Add permissions,’ attach ‘S3ReadOnlyAccess’ policy and click ‘Next.’
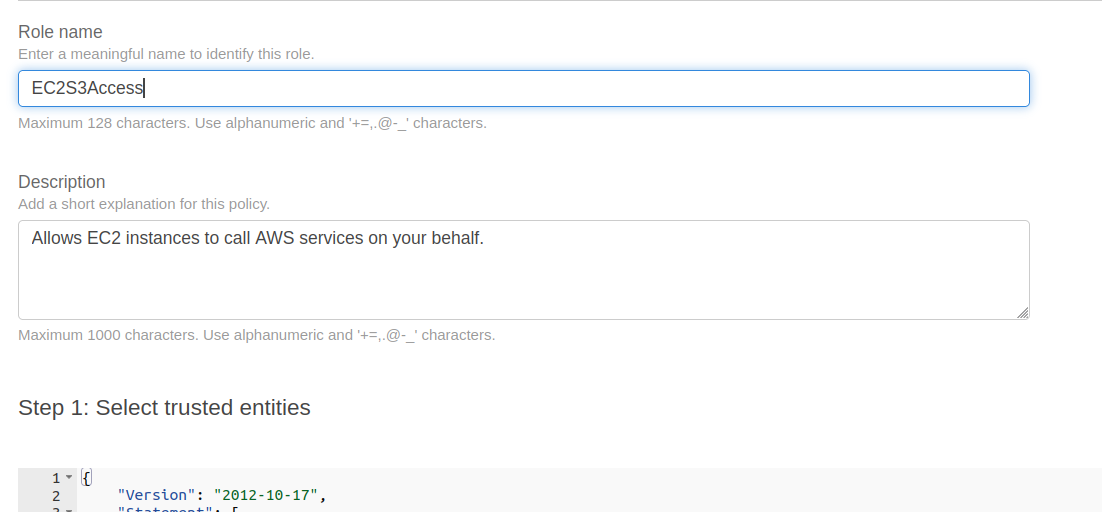
Step 4. Name the role ‘EC2S3Access,’ optionally adding a description.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"sts:AssumeRole"
],
"Principal": {
"Service": [
"ec2.amazonaws.com"
]
}
}
]
}
Step 5. Click ‘Create role’ to complete the setup.
Adding IAM Policy for the User
We will now create a policy for the IAM user, granting full EC2 access and permission to associate the ‘EC2S3Access’ role:
Step 1. Go to the IAM dashboard, select ‘Policies,’ and click ‘Create policy.’
Step 2. In the Create policy wizard’s JSON tab, paste the following policy:
{
"Version": "2012-10-17",
"Statement": [{
"Effect":"Allow",
"Action":["ec2:*"],
"Resource":"*"
},
{
"Effect":"Allow",
"Action":"iam:PassRole",
"Resource":"arn:aws:iam::account_ID:role/EC2S3Access"
}]
}
Replace ‘account_ID’ with the actual account ID. Click ‘Next: Tags.’
Step 3. Add any optional ‘Tags’ and click ‘Next: Review.’
Step 4. Name the policy (‘iam_user_policy’) and click ‘Create policy.’
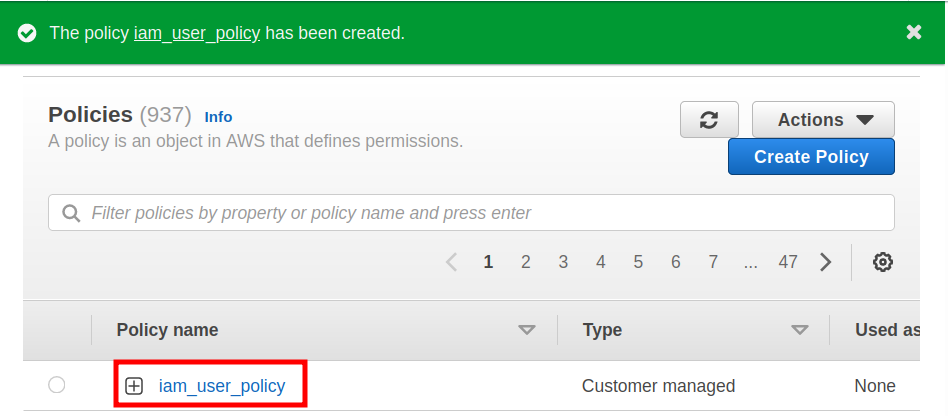
Step 5. Attach the policy to the IAM user.
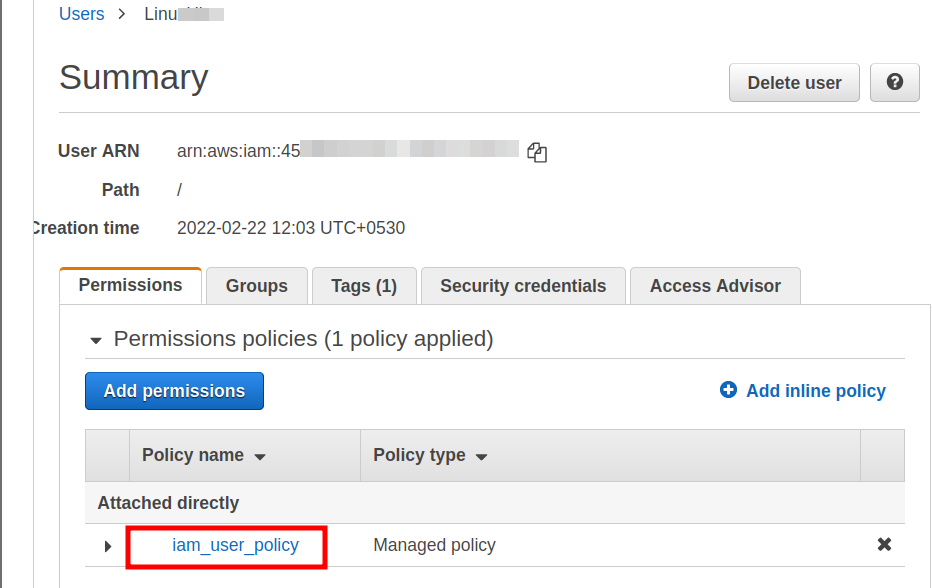
Attaching the Role to the Instance
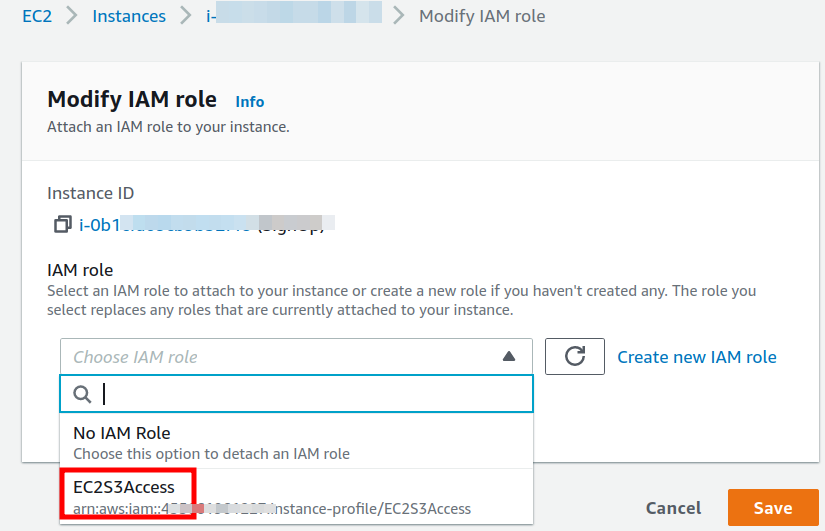
Finally, attach the role ‘EC2S3Access’ to an already running EC2 instance.
For running instances, navigate to EC2 console, select the target instance, and choose ‘Action > Security > Modify IAM role.’ Select ‘EC2S3Access’ and click ‘Save.’
Testing the Setup
To verify the setup, your EC2 instance should be able to access an S3 bucket.
Create a bucket from the administrator account. Log into the EC2 instance, install and configure AWS CLI, and run:
$ aws s3 ls
Run the command from a different machine; it should return an access error, confirming limited permissions.
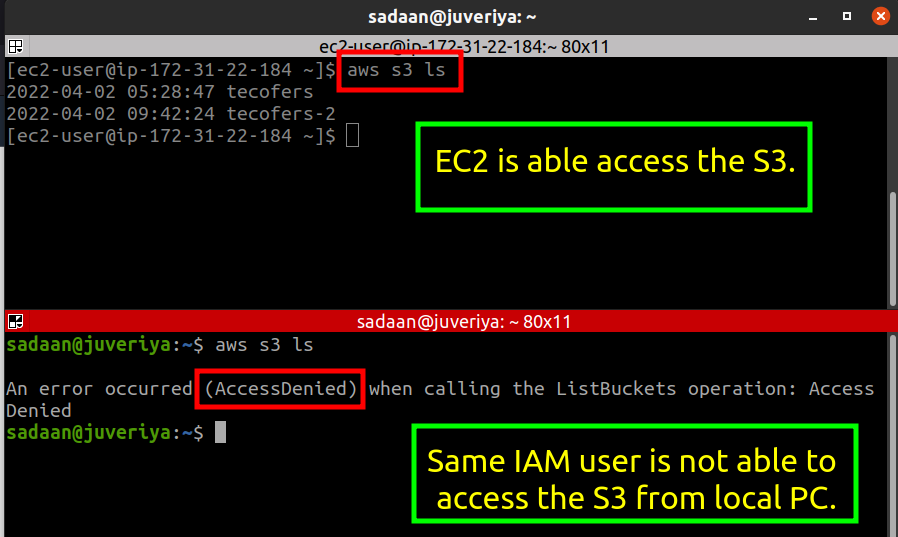
The error occurs because access permission is granted only to the EC2 instance.
Conclusion
This guide covered using PassRole permission to apply least privilege principles in AWS IAM, demonstrating how an EC2 instance can access an S3 bucket securely.
FAQ
- What is the IAM PassRole permission?
- It is an authorization allowing users to delegate role permissions to AWS services.
- Can roles be modified after creation?
- Yes, roles can be modified after creation, including changing policies and trust relationships.
- How do temporary credentials work?
- They are granted via assumed roles and provide secure, short-term access to AWS resources.