SFTPGo is a sophisticated and open-source SFTP server that offers extensive features and is highly configurable. It also supports optional protocols such as HTTP/S, FTP/S, and WebDAV, while allowing integration with various storage backends like local filesystems, encrypted local filesystems, S3 Object Storage, Google Cloud Storage, Azure Blob Storage, and even other SFTP servers.
For a detailed list of features, visit the GitHub project page.
SFTPGo is available on multiple operating systems including Linux, Windows, macOS, and FreeBSD. This guide will walk you through the installation process on an Ubuntu 22.04 system and highlight the main new features introduced in version 2.3.0.
Prerequisites
- Running Ubuntu server version 22.04.
- A non-root user equipped with sudo privileges.
Setting Up UFW Firewall
For enhanced security, it’s advisable to install and configure UFW firewall on your system. Use the following command to install the UFW firewall:
sudo apt install ufw -y
By default, SFTPGo utilizes the following TCP ports:
- 2022 for the SFTP service.
- 8080 for the web admin interfaces.
Additionally, do not forget to allow the OpenSSH port for server administration.
Allow these ports with the commands below:
sudo ufw allow OpenSSH sudo ufw allow 2022/tcp sudo ufw allow 8080/tcp
Enable the firewall to start on boot:
sudo ufw enable
Verify the firewall status:
sudo ufw status
Your output should be similar to:
Status: active To Action From -- ------ ---- OpenSSH ALLOW Anywhere 2022/tcp ALLOW Anywhere 8080/tcp ALLOW Anywhere OpenSSH (v6) ALLOW Anywhere (v6) 2022/tcp (v6) ALLOW Anywhere (v6) 8080/tcp (v6) ALLOW Anywhere (v6)
Installing SFTPGo on Ubuntu 22.04
SFTPGo can be installed from its PPA.
Add the PPA with the following commands:
sudo add-apt-repository ppa:sftpgo/sftpgo sudo apt update
Proceed with the installation:
sudo apt install sftpgo
After installation, verify that SFTPGo is running through:
systemctl status sftpgo
Completing SFTPGo Installation
To complete the installation, open a web browser and visit: “http://<your server IP/hostname:8080>/“.
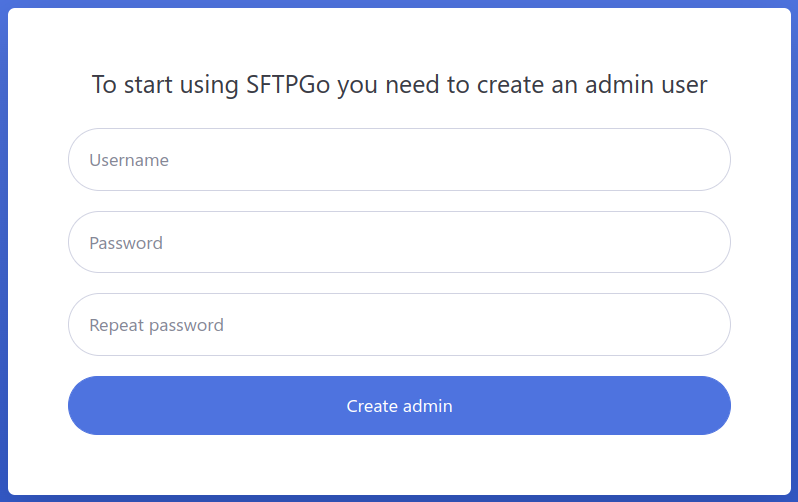
Enter your admin username and password, then click the “Create Admin” button. The new admin account will log in automatically, enabling you to create SFTPGo users.
For user creation details, refer to the Getting Started Guide.
New Features in v2.3.0
Groups
SFTPGo now supports user groups, simplifying management by allowing shared settings among users within a group. The two types of groups are primary and secondary, with different inheritance settings.
For comprehensive details, see the official documentation.
Consider a scenario where you need:
- Restriction of each user to a personal local directory.
- A file upload size limit of 1GB per user.
- An S3 virtual folder path for user files, accessible exclusively to them.
- A shared folder with specified permissions based on user group membership.
Group Configuration
Set up your system according to these needs by following these steps:
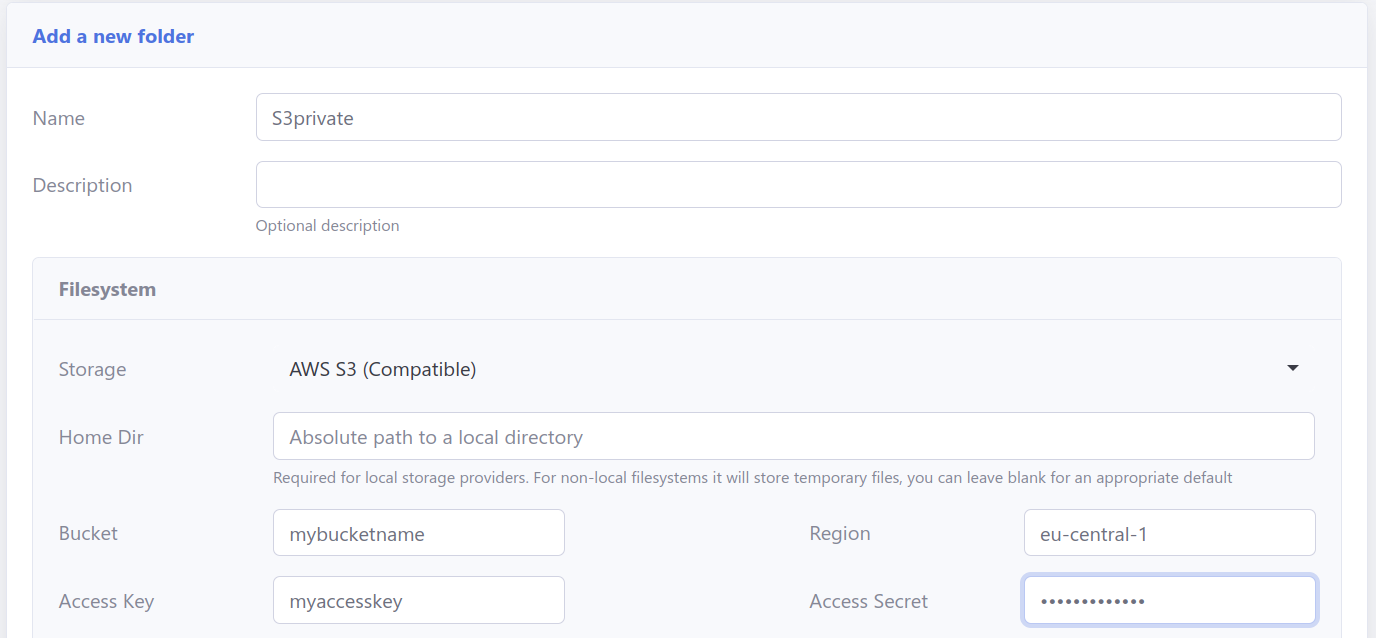
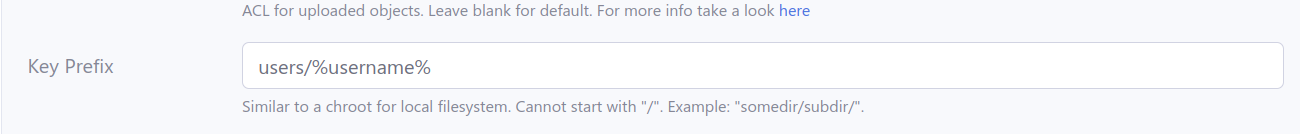
1. Define “S3private” and “S3shared” folders with AWS S3 settings. Use “users/%username%/” and “shared/” as key prefixes respectively.
2. Create a “Primary” group, set the home directory to “/srv/sftpgo/data/%username%“, and configure folder permissions.
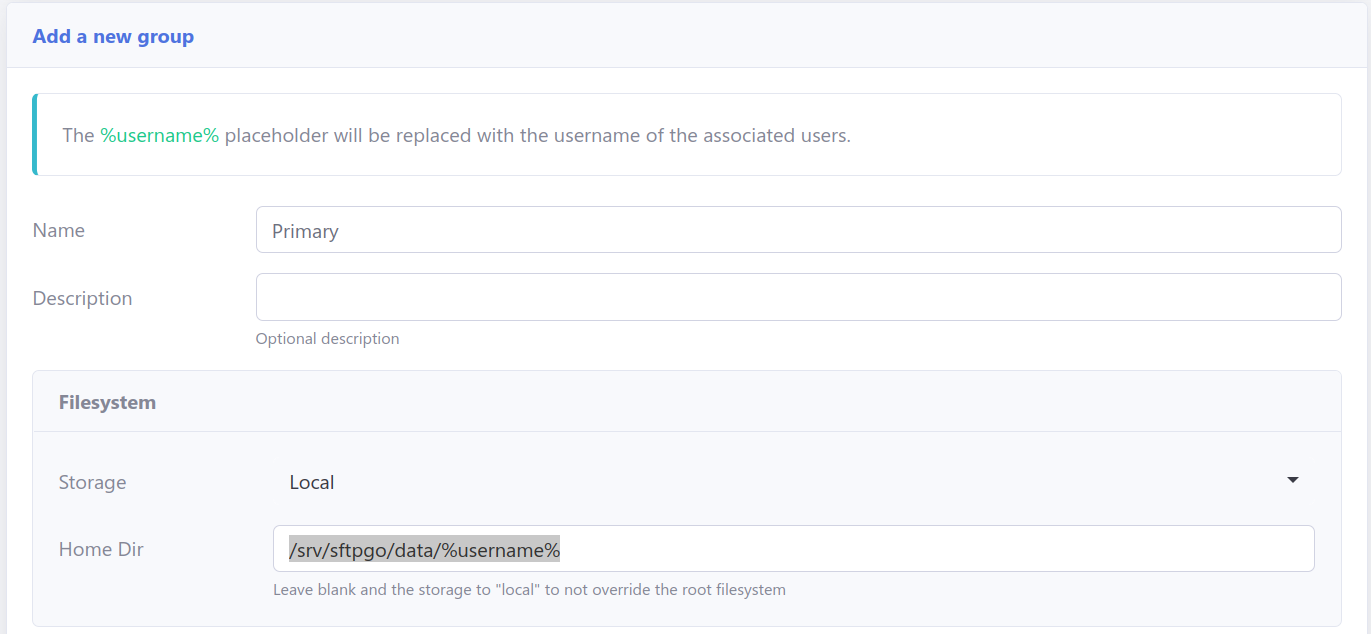
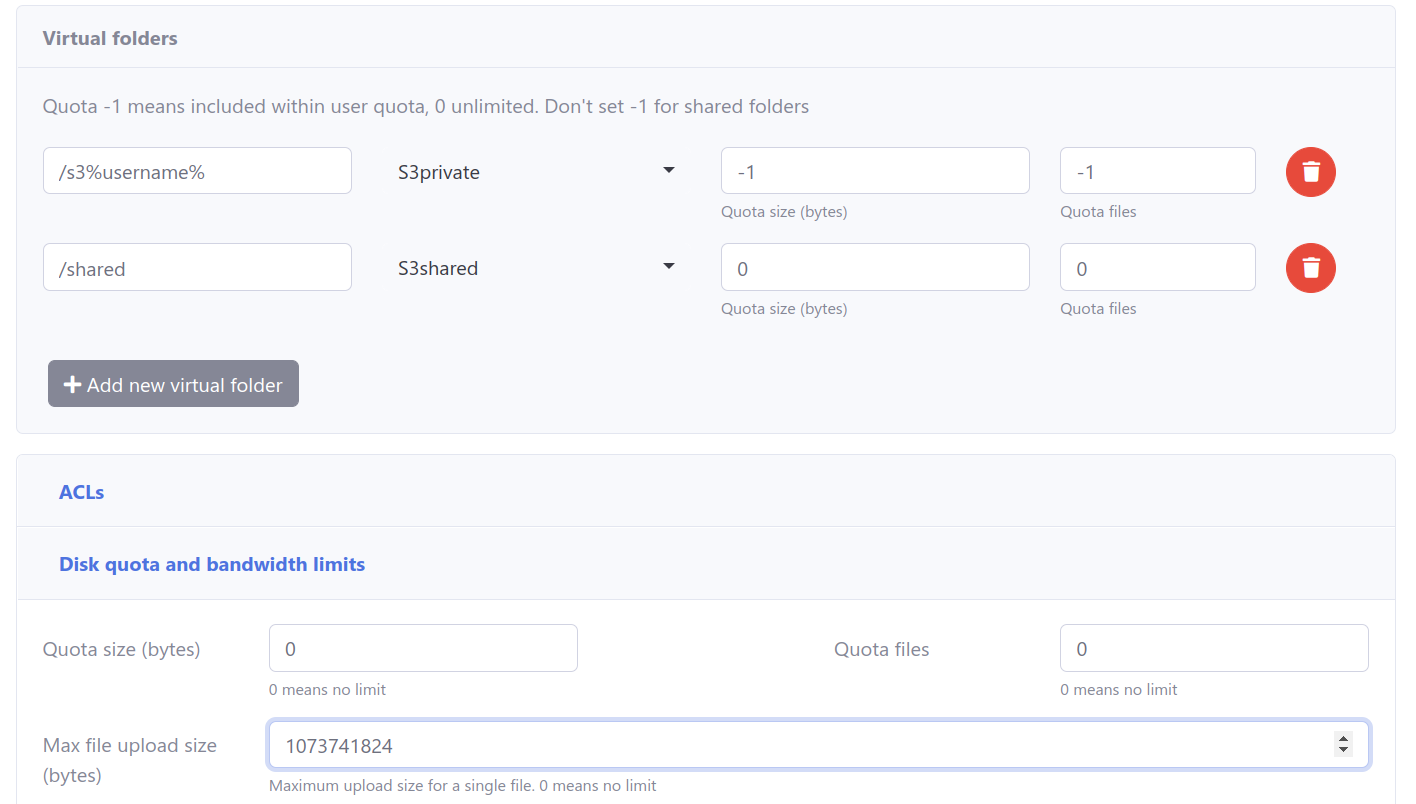
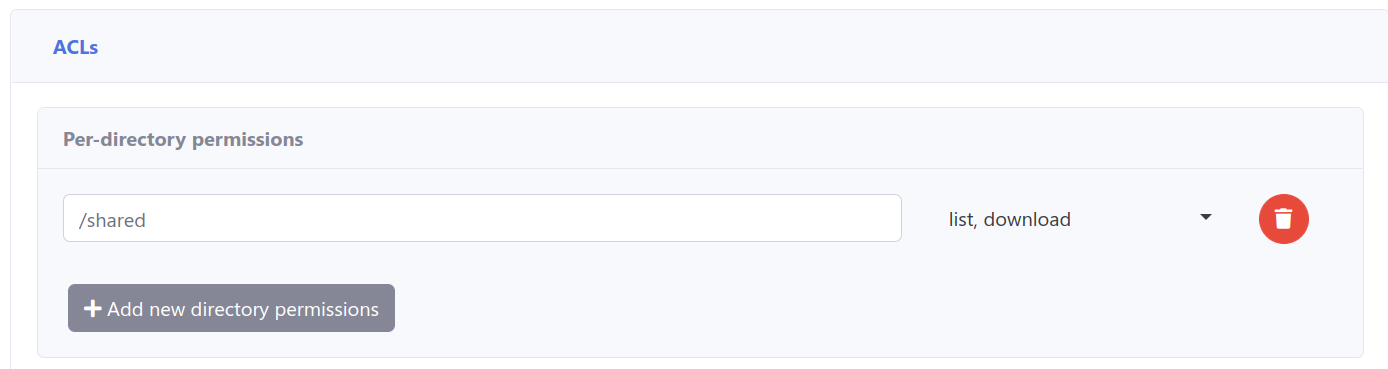
3. Add a “SharedReadOnly” group with partial ACL permissions for shared folders.
4. Create users and designate them to relevant groups for desired access.
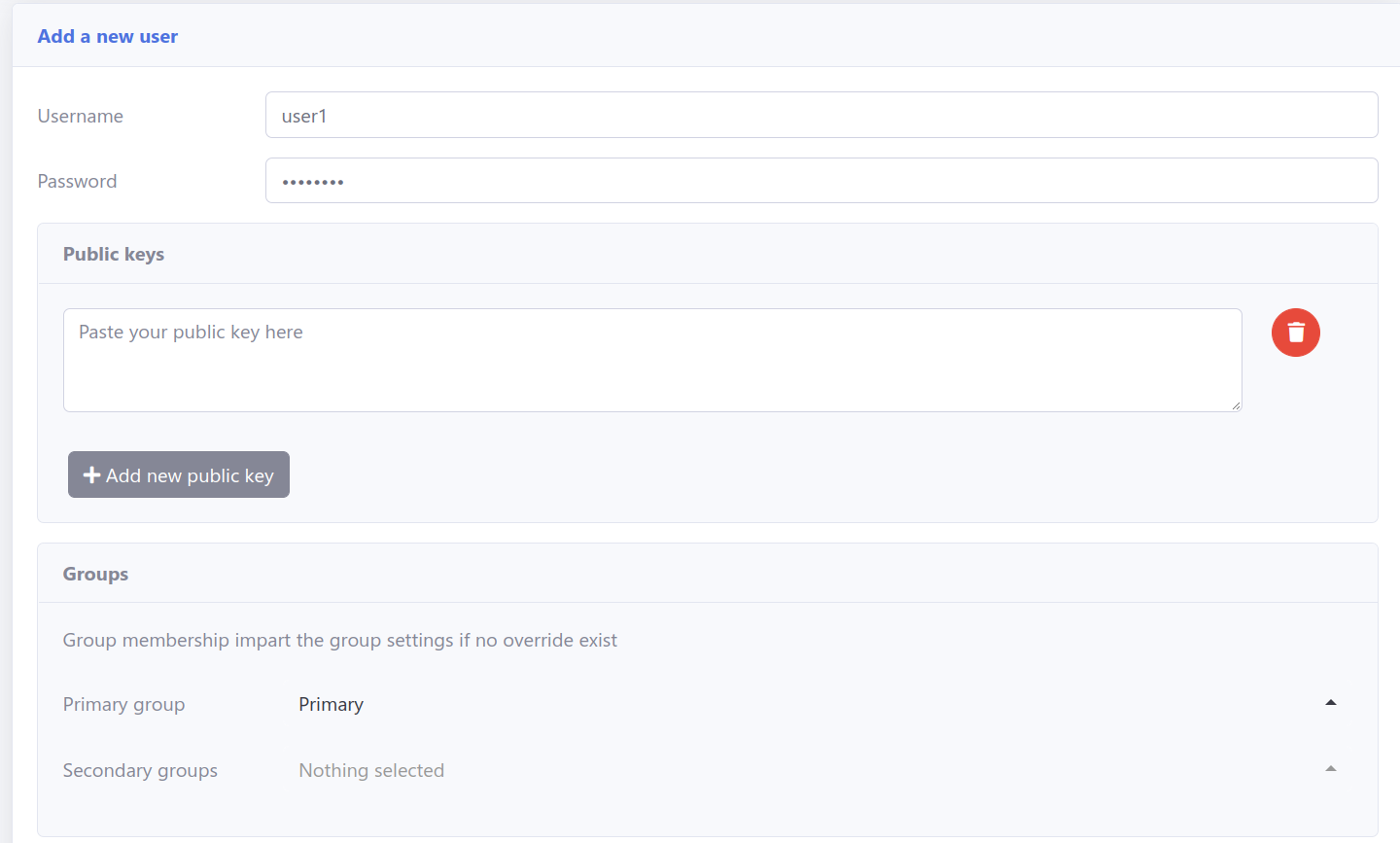
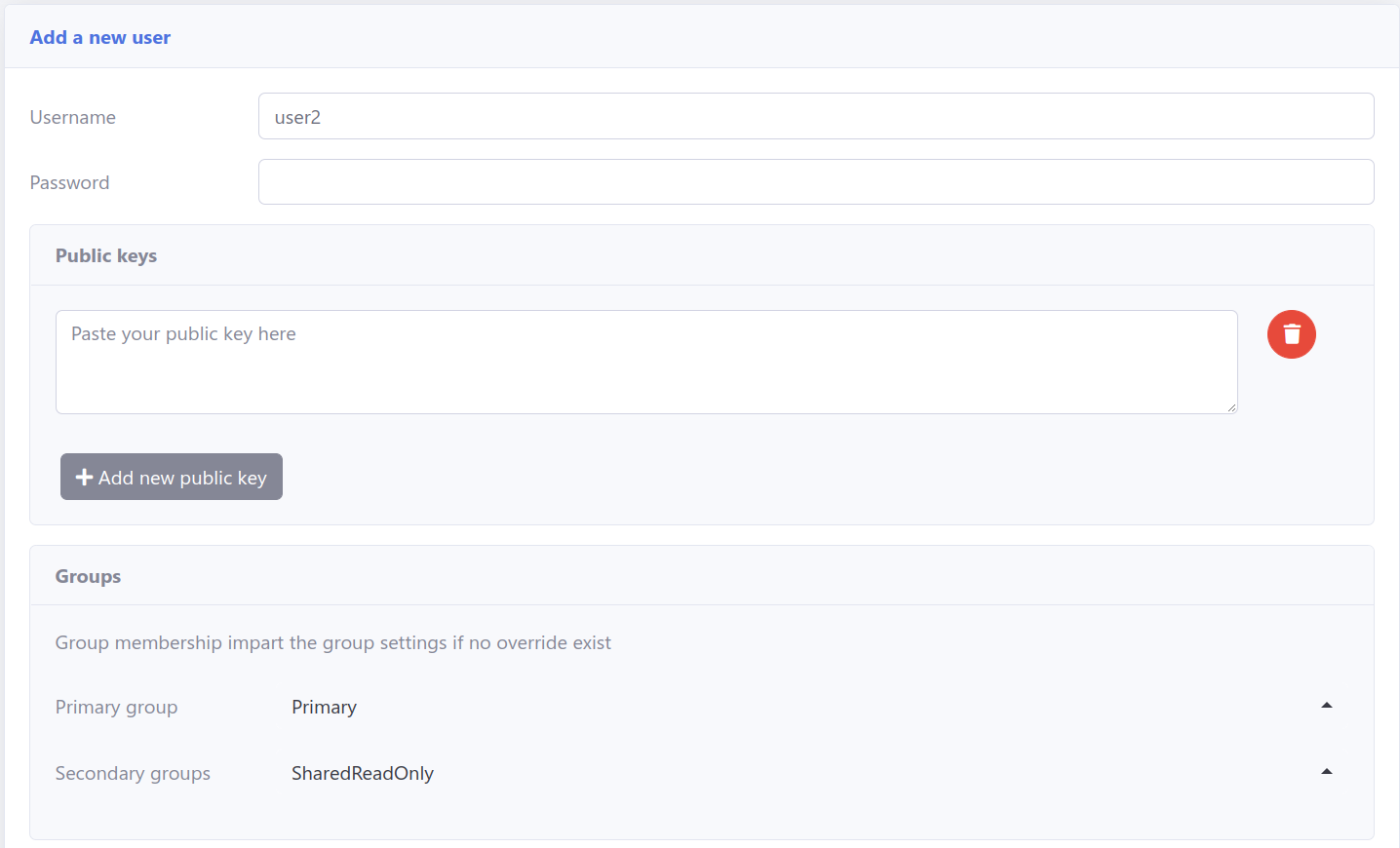
Optionally, utilize templates to add multiple users efficiently.
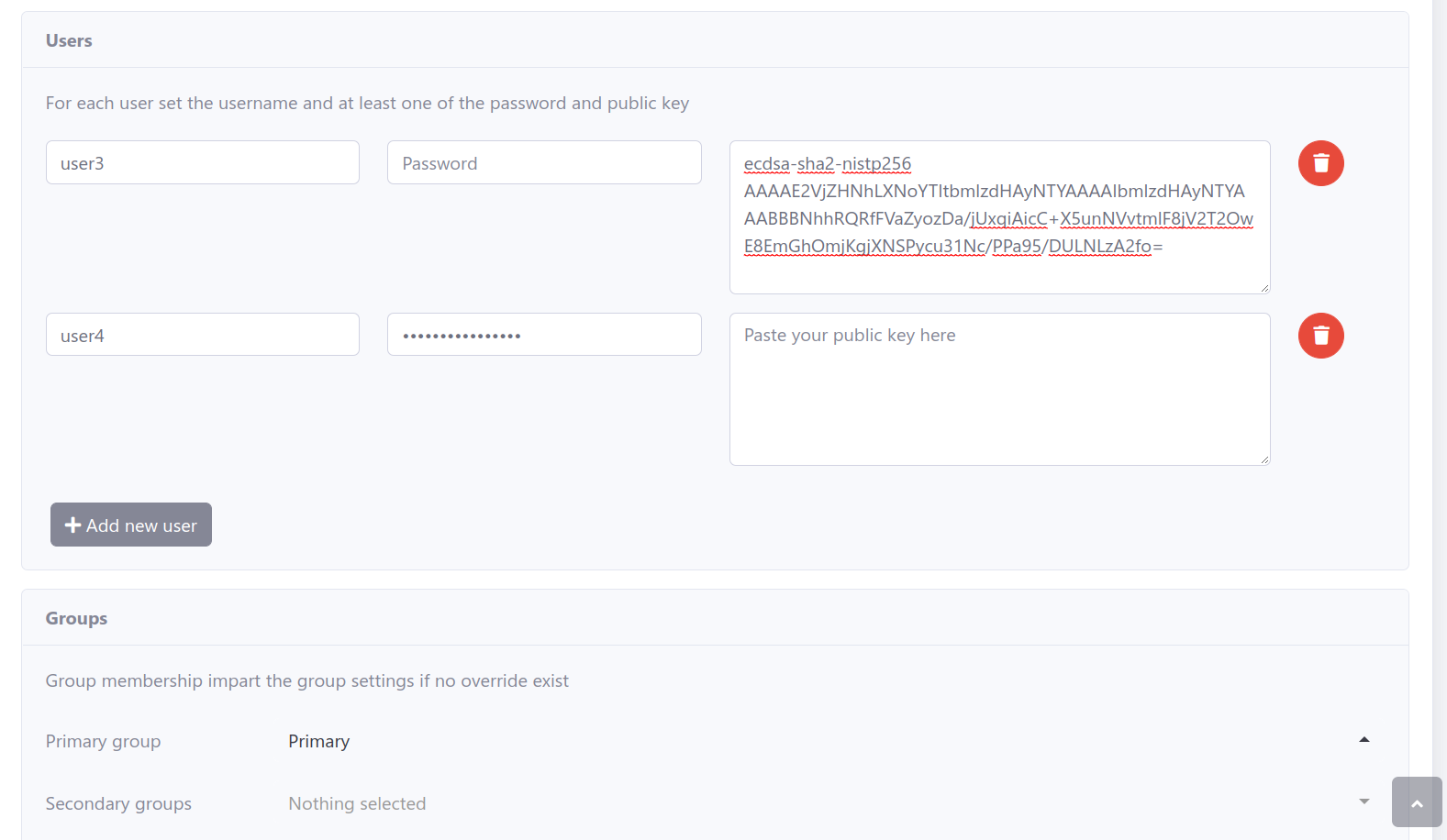
Test the configuration by logging in through any SFTP client to ensure the requirements are met.
External Shares
With improved file-sharing capabilities, external users can access files even without an account. You can set the access modes to read-only, write-only, or both.
Creating and managing shares:
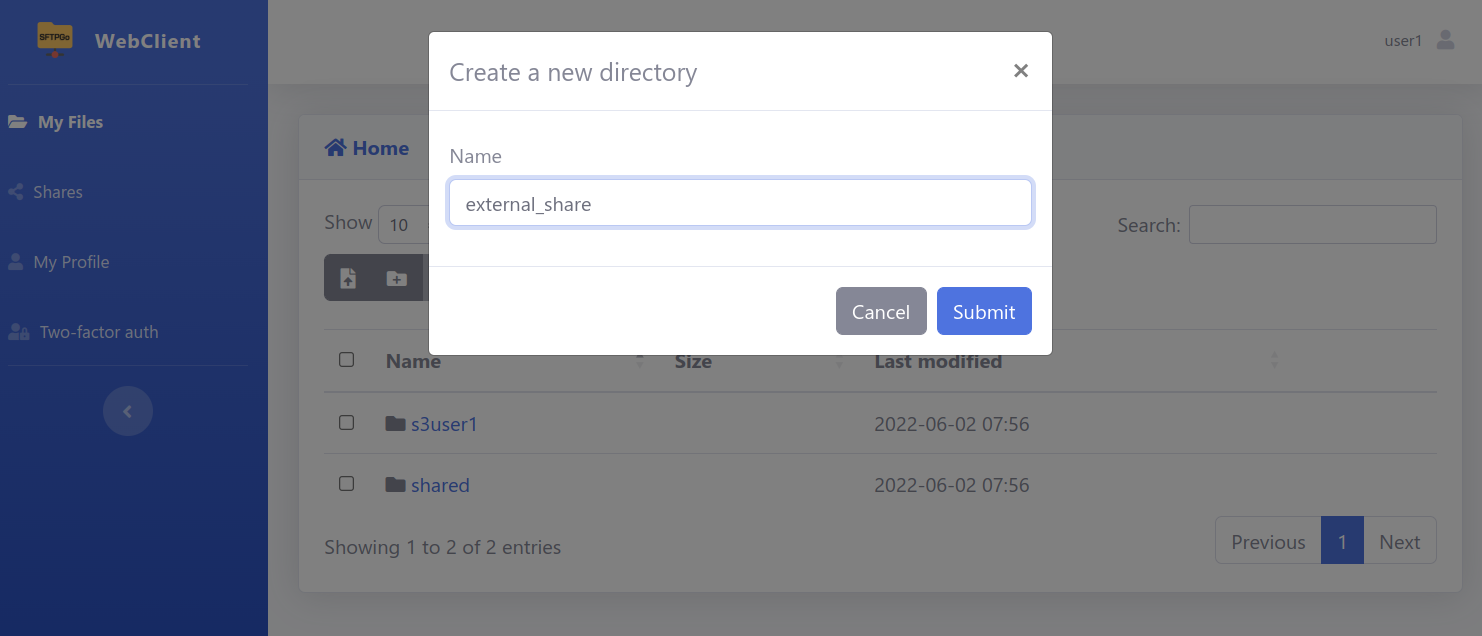
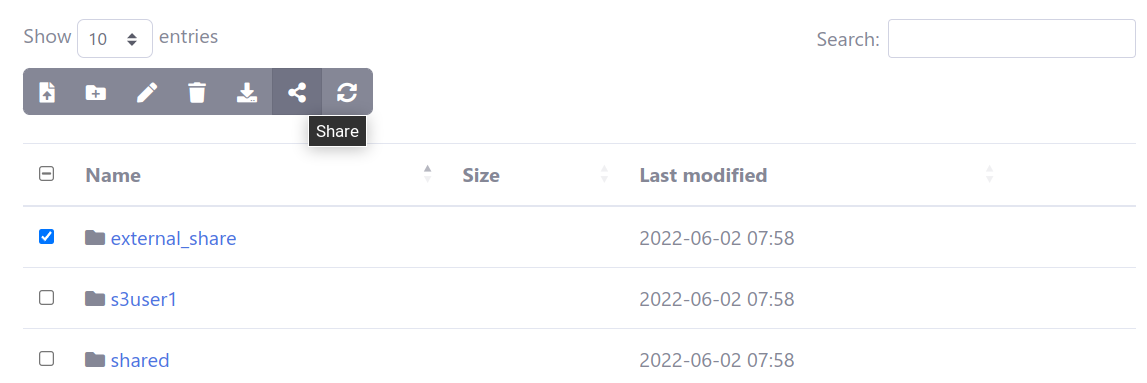
Create an “external_share” folder, populate it with files, and share the directory:
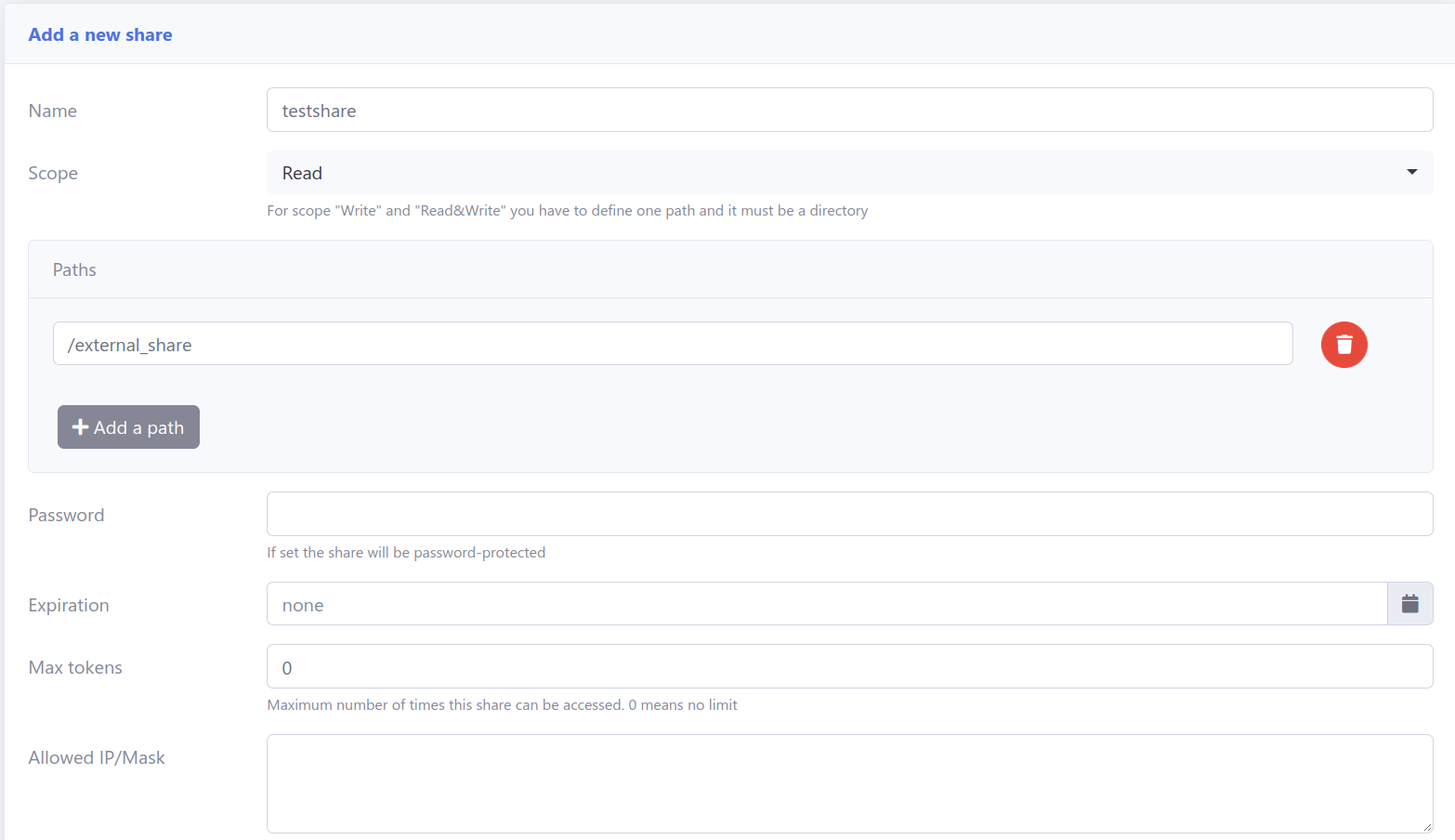
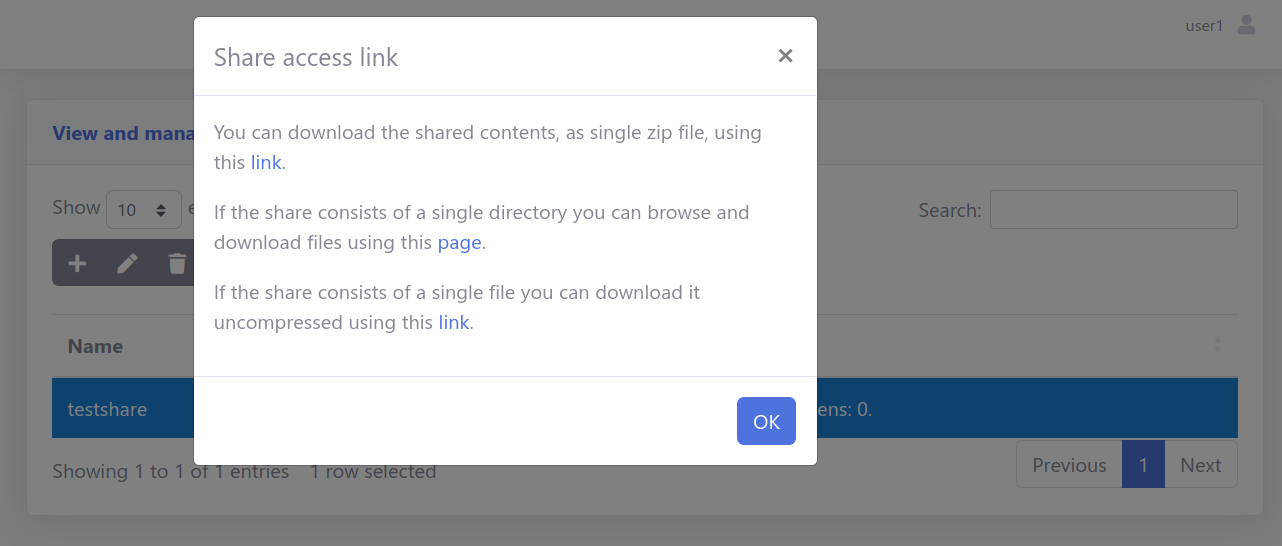
Share links are generated, which can be provided to external users:
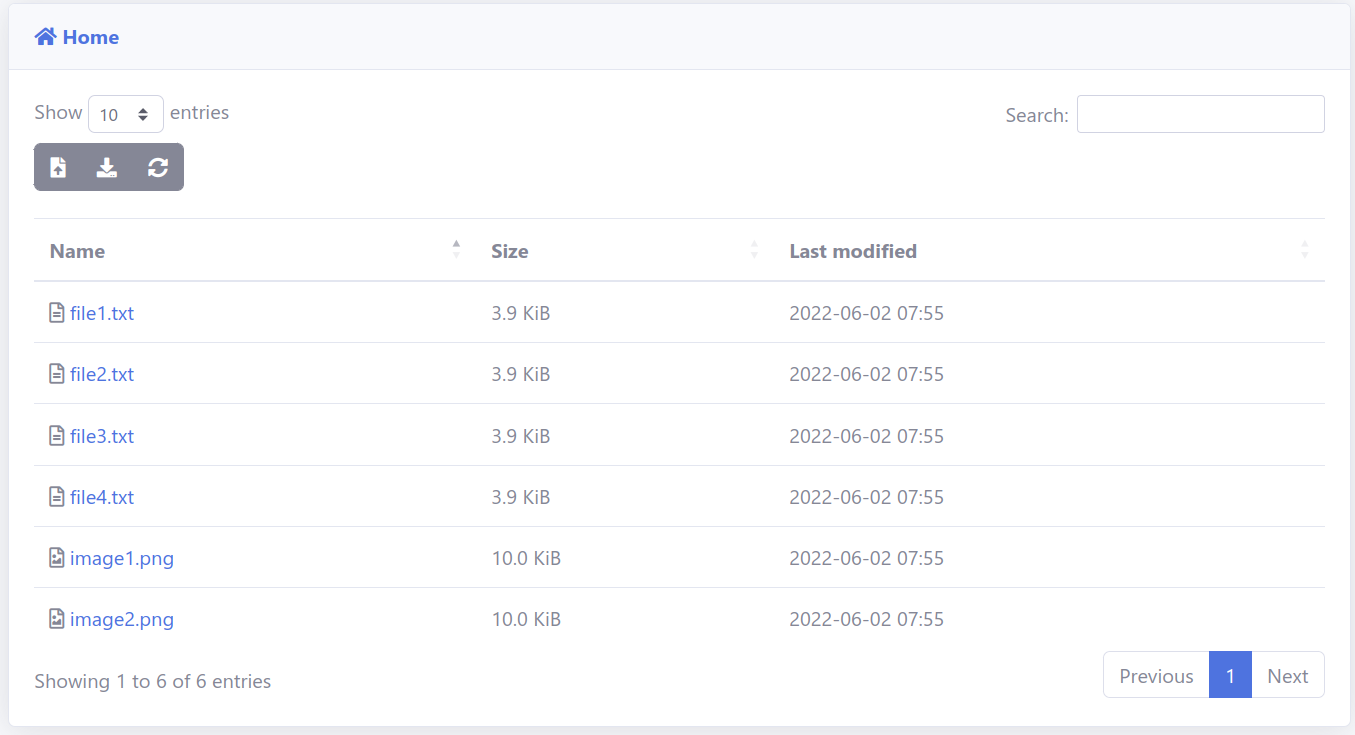
Branding
Customize SFTPGo web UIs to your brand’s specifics by adjusting settings in /etc/sftpgo/sftpgo.json.
"branding": {
"web_admin": {
"name": "",
"short_name": "",
"favicon_path": "",
"logo_path": "",
"login_image_path": "",
"disclaimer_name": "",
"disclaimer_path": "",
"default_css": "",
"extra_css": []
},
"web_client": {
"name": "",
"short_name": "",
"favicon_path": "",
"logo_path": "",
"login_image_path": "",
"disclaimer_name": "",
"disclaimer_path": "",
"default_css": "",
"extra_css": []
}
}
Customize the favicon, logos, and CSS as needed. More details about configuring over environment variables are available on the SFTPGo configuration guide.
OpenID Connect
SFTPGo integrates with OpenID Connect Identity Providers, mapping them to SFTPGo users/admins for seamless login experiences. Users can be automatically created post-login using custom logic.
For integration steps, refer to Keycloak in the official documentation. It has been tested with Google Identity, Azure AD, Auth0, OneLogin, among others.
ACME Support
SFTPGo now has built-in ACME support for managing Let’s Encrypt TLS certificates across different services, enabling secure connections.
Configure it by ensuring domain validation, acquiring a domain name, and following example settings provided in the guide. After setup, certificates are auto-renewed as needed.
Geo-IP Filtering
The Geo-IP filtering plugin allows for connection access based on client IP geographical location, using MaxMind’s GeoLite2 and GeoIP2 databases.
Configuration requires specifying inclusion/exclusion IPs based on country codes:
"plugins": [
{
"type": "ipfilter",
"cmd": "/usr/local/bin/sftpgo-plugin-geoipfilter-linux-amd64",
"args": ["serve", "--db-file", "/var/lib/sftpgo/GeoLite2-Country.mmdb", "--allowed-countries", "IT"],
"sha256sum": "",
"auto_mtls": true
}
]
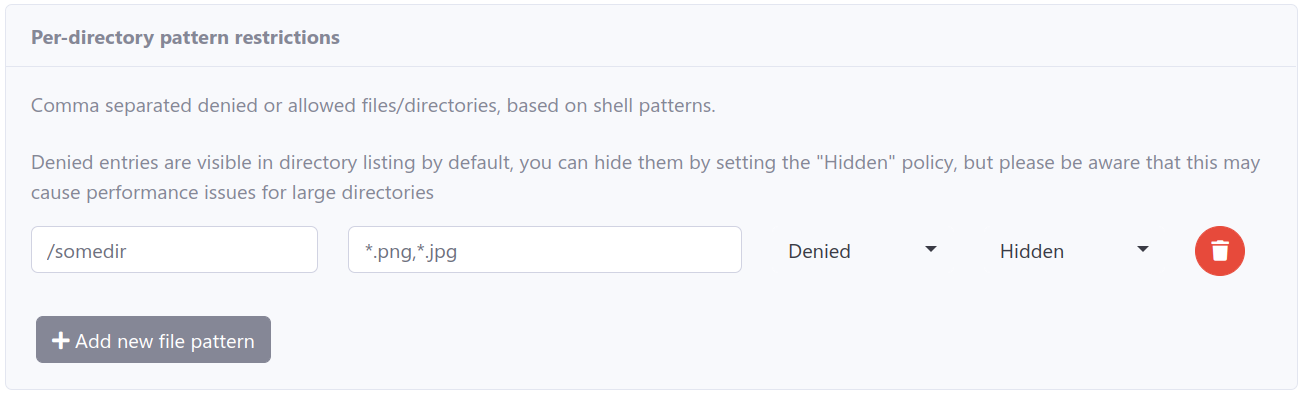
Shell Pattern File/Directory Restrictions
SFTPGo enables shell pattern restrictions on directories or files as a powerful access control measure. Specify shell-like patterns to hide or deny access to certain files.
Implement restrictions at a per-directory level via the user’s ACL section in the interface:
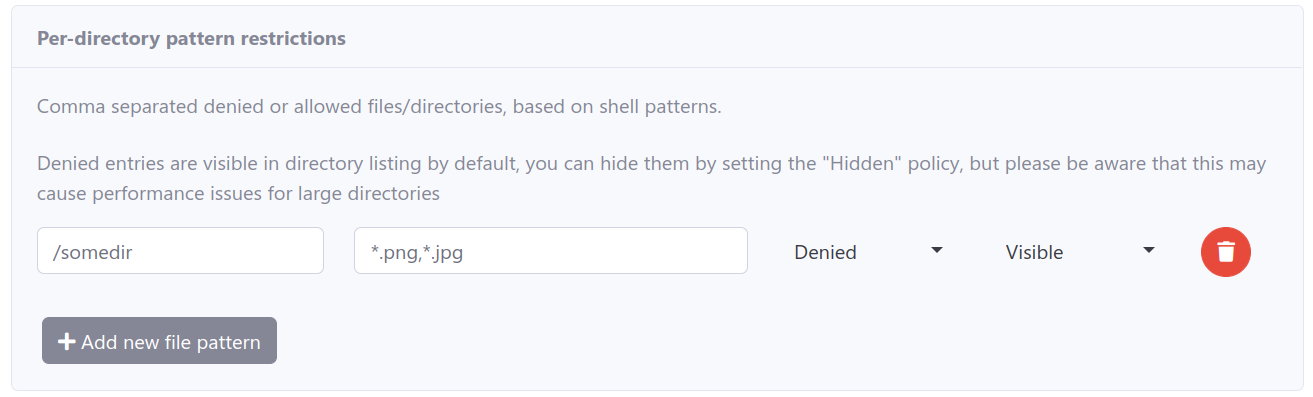
FAQ
What is SFTPGo?
SFTPGo is an open-source, fully-featured SFTP server compatible with HTTP/S, FTP/S, and WebDAV, alongside multiple storage integrations.
Is SFTPGo compatible with other operating systems?
Yes, SFTPGo is available for Linux, Windows, macOS, and FreeBSD.
What are the minimum system requirements for installing SFTPGo?
An updated Linux server, such as Ubuntu 22.04, and a non-root user with sudo privileges.
Can I access SFTPGo through a web interface?
Yes, SFTPGo provides a web-based interface for user management and administrative tasks.
What if I face issues with installation?
Ensure all dependencies are installed, and refer to the official SFTPGo GitHub page or community forums for assistance.