The Terraform Registry serves as a comprehensive platform where you can discover and integrate various providers and modules, essentially reusable Terraform configurations, into your infrastructure workflows. Developed by HashiCorp, along with contributions from third-party vendors and the Terraform community, this registry offers a plethora of plugins for efficiently managing diverse infrastructure APIs. Moreover, it provides ready-to-use modules for swiftly building commonly deployed infrastructure components, alongside insights into developing optimized Terraform code.
What Will We Cover?
This tutorial will guide you on leveraging modules from the Terraform Registry by creating an EC2 instance on AWS as an example.
Pre-requisites
To follow along with this tutorial, ensure you have:
- Terraform installed on your local system.
- A fundamental understanding of Terraform modules.
- An active AWS account.
Using Modules from the Terraform Registry
The Terraform Registry maintains modules for various providers. To find modules, visit the Terraform Registry page. Only verified modules appear by default in search results, as they are evaluated for compatibility and stability by HashiCorp. You can also opt to view unverified modules using search filtering options.
Referring to modules from the Terraform Registry in your Terraform configurations follows this pattern:
<NAMESPACE>/<Module Name>/<Provider Name>
For example, consider this module usage from the Terraform Registry:
module "vpc" {
source = "terraform-aws-modules/vpc/aws"
}
In the example above, a VPC module for AWS is utilized from the Terraform Registry. Executing the terraform init command fetches and stores the modules as referenced in your Terraform configurations.
The Terraform Registry accommodates both public and private module usage. Public modules are freely available, while private modules can be handled via a private registry.
Exploring the Terraform Registry
The module page offers concise information about each module, such as its description, publishing date, source code URL, and download statistics. Multiple tabs for Readme, Inputs, Outputs, Dependencies, and Resources assist in determining the necessary variables for your implementations.
Example configurations are also provided; in this guide, we’ll reference a module for creating an EC2 instance. Before you proceed, review the module’s source code by visiting its URL. You’ll find key files such as main.tf, outputs.tf, and variables.tf, which define the EC2 instance parameters and the corresponding input and output values.
Launching an EC2 Instance Using a Module
Let’s demonstrate using a module from the Terraform Registry to launch an EC2 instance, utilizing the ‘terraform-aws-modules’ for this task.
Step 1: Visit the Terraform Registry webpage and search for the AWS module for EC2:
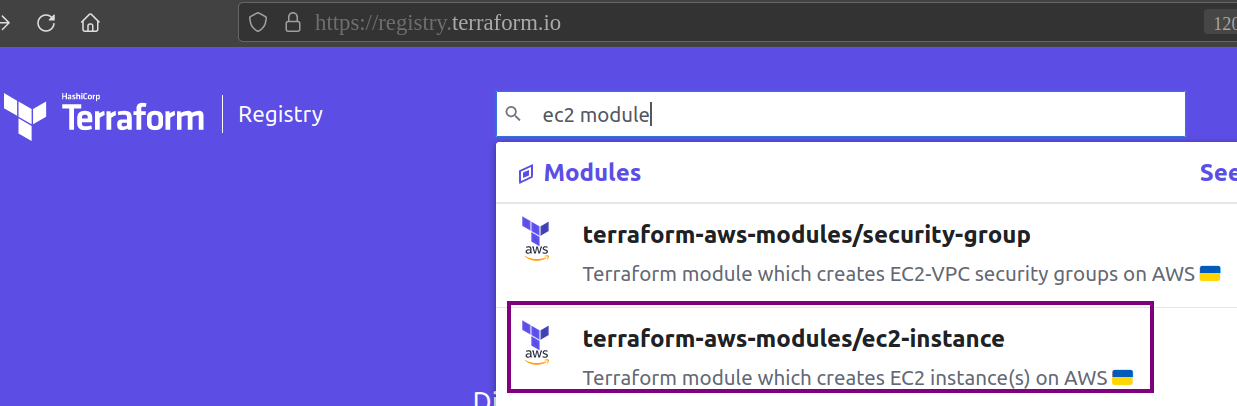
Step 2: Click on the ‘terraform-aws-modules/ec2-instance’ result. This module aids in launching an AWS EC2 instance.
Create a local configuration file (myinstance.tf) that uses this module, as illustrated below:
$ nano myinstance.tf
provider "aws" {
region = "us-east-1"
}
module "ec2_instance" {
source = "terraform-aws-modules/ec2-instance/aws"
version = "~> 3.0"
name = "single-instance"
ami = "ami-0022f774911c1d690"
instance_type = "t2.micro"
availability_zone ="us-east-1a"
key_name = "Your-Key-pair-name"
monitoring = true
vpc_security_group_ids = ["Security-Group-ID"]
putin_khuylo = true
tags = {
Terraform = "true"
Environment = "dev"
}
}
The configuration uses two crucial arguments:
- Source: Identifies the Terraform module you’re using. In the provided example, this argument points to the module in the Terraform Registry. You can also use local modules, URLs, or other sources.
- Version: While optional, specifying a version ensures you’re working with a particular module version, offering more reliable deployments by avoiding unexpected updates.
Initialize the directory with your local ‘myinstance.tf’ file using the following command:
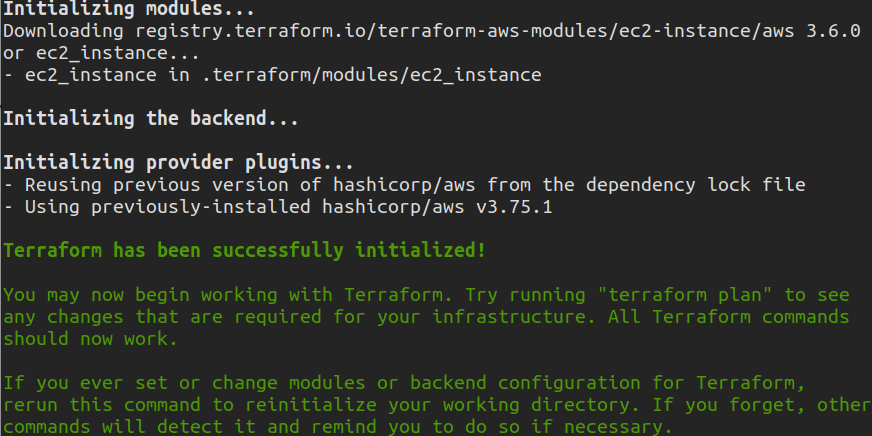
Proceed with terraform plan or apply changes directly using terraform apply:
$ terraform apply
Confirm your action by entering ‘yes’ when prompted. The changes will begin to apply.
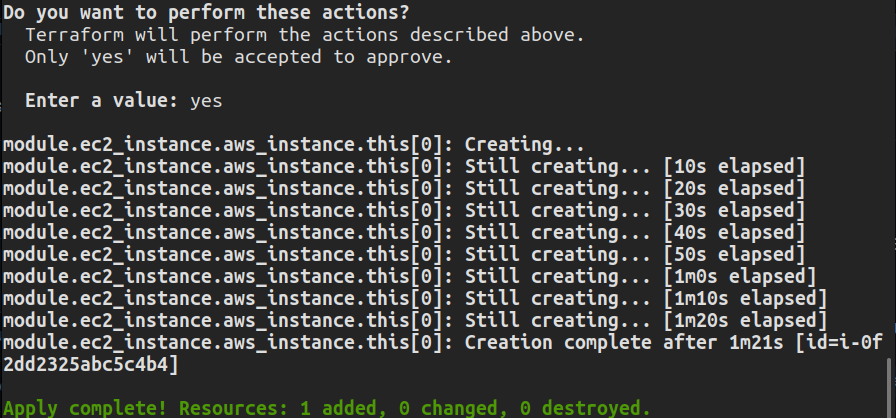
No need to manually create variables.tf or outputs.tf; you simply reference required variables from the repository. Subsequently, verify your instance creation from the EC2 dashboard in your AWS Management Console.
Conclusion
This guide outlined how to effectively employ Terraform Registry modules. You might extend your learning by configuring a VPC using a similar Terraform module.
FAQs
1. What is the Terraform Registry?
The Terraform Registry is a platform for discovering and utilizing providers and modules created by the Terraform community, HashiCorp, and third-party vendors.
2. Why use the Terraform Registry?
It helps streamline infrastructure management by providing reusable modules and verified providers, enabling quick and efficient development of Terraform-based configurations.
3. Are there private modules available?
Yes, aside from public modules, you can also publish and use private modules through a private registry option.
4. How can I trust the modules provided?
Verified modules are examined by HashiCorp for stability and compatibility. You can identify them as they appear in search results on the Terraform Registry by default.
5. What if I encounter issues using a module?
Every module page includes a Readme section that provides detailed instructions. Additionally, you can check the module’s issues page on GitHub for resolutions to common problems.