In this guide, we’ll explore how to analyze network packets on Linux using Tcpdump and Wireshark. This tutorial uses Ubuntu but is applicable to other Linux distributions as well.
Why Use Tcpdump?
Why consider Tcpdump when Wireshark offers robust features already? Simply put, Tcpdump is more convenient for capturing packets on remote or headless machines where Wireshark isn’t available. In such scenarios, Tcpdump’s command-line functionality is invaluable. To explore various Tcpdump options, consult the man pages.
What Is Tcpdump?
Tcpdump is a command-line packet analyzer. It essentially performs the same task as Wireshark—capturing and analyzing network traffic—but without the graphical interface. Users might initially find Tcpdump’s command-line nature challenging due to its complex syntax and commands.
Tutorial Outline
This guide demonstrates how to integrate Tcpdump with Wireshark. Here’s an outline of the steps we’ll cover:
- Connecting to the remote machine (Host 2) via SSH.
- Capturing traffic with Tcpdump and saving the capture.
- Transferring the capture file to the local machine (Host 1) with Wireshark installed.
- Analyzing the Tcpdump captured session with Wireshark.
Pre-Flight Check
We’ll utilize two Ubuntu 20.04 machines configured as follows:
- Host 1 (Local Machine): 192.168.186.150
- Host 2 (Remote Machine): 192.168.186.201
Ensure the following requirements are met on any Linux system used:
- Local host (Host 1) with Wireshark installed and SSH configured.
- SSH access from the local host (Host 1) to the remote host (Host 2).
- Tcpdump and SSH should be configured on the remote host (Host 2).
- Sudo access on Host 2 for running Tcpdump, and on Host 1 if Wireshark needs it.
Step-by-Step Guide
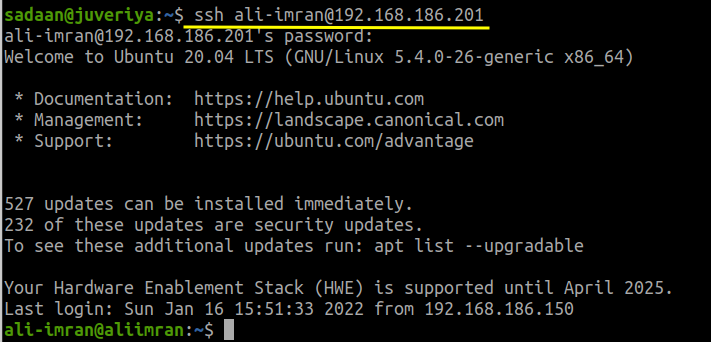
Begin by connecting from your local machine (Host 1) to the remote machine (Host 2) using SSH:
$ ssh 'user_name'@'IP_of_Host2'
Replace ‘user_name’ with the username on Host 2 and ‘IP_of_Host2’ with the IP address of Host 2. Refer to the image below as a reference:
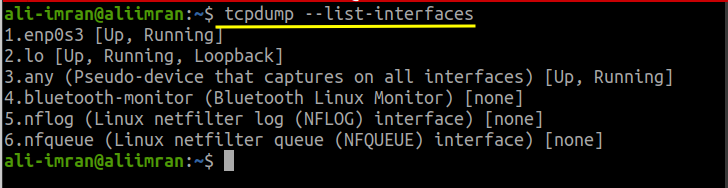
Next, verify available interfaces for packet capturing on the remote machine:
$ tcpdump --list-interfaces
Sample Output:
1.enp0s3 [Up, Running] 2.lo [Up, Running, Loopback] 3.any (Pseudo-device that captures on all interfaces) [Up, Running] 4.eno1 [Up] 5.bluetooth-monitor (Bluetooth Linux Monitor) [none] 6.nflog (Linux netfilter log (NFLOG) interface) [none] 7.nfqueue (Linux netfilter queue (NFQUEUE) interface) [none] 8.bluetooth0 (Bluetooth adapter number 0) [none]
Choose the interface ‘enp0s3’ for capturing. To terminate capturing, press ‘Ctrl+C’. Use the command:
$ sudo tcpdump -s 65535 -i enp0s3 -w my_remote_capture.pcap
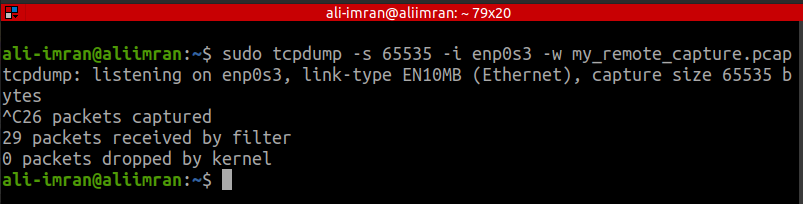
Here’s a breakdown of the command options:
- -s: Captures packets at full length instead of 68 or 96 bytes.
- -i: Specifies the interface to listen on.
- -w: Writes captured packets to a file instead of displaying them on the terminal.
The captured traffic is saved in ‘my_remote_capture.pcap’. Transfer this file to Host 1 using SCP:
$ scp my_remote_capture.pcap 'username'@'IP_of_remote_machine':
‘username’ and ‘IP_of_remote_machine’ refer to the user and IP on Host 1 respectively.
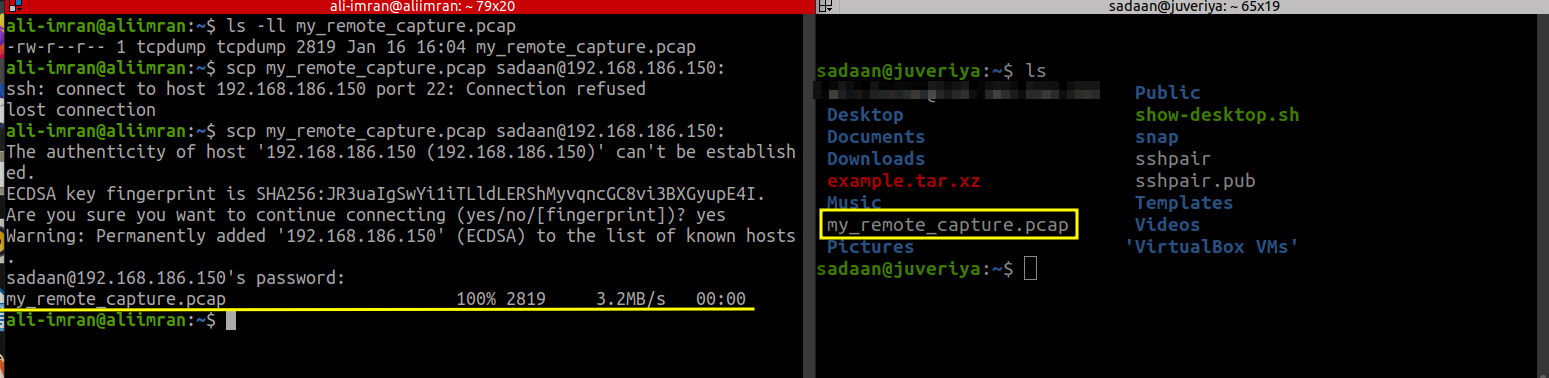
On your local machine (Host 1), verify the file transfer and open it using Wireshark:
Analyzing the Capture File
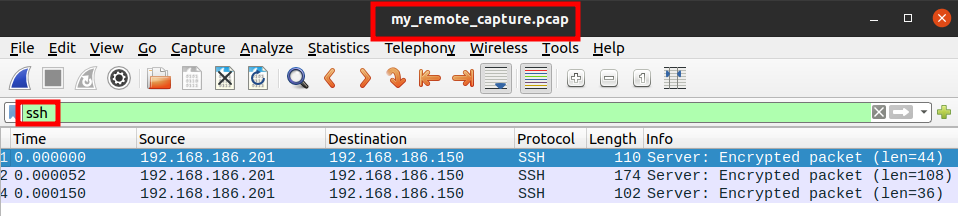
Apply a display filter for SSH packets on the capture file since we connected using SSH:
Display filter: ssh
Conclusion
Congratulations! You’ve successfully learned how to capture packets on a remote machine using Tcpdump and analyze them with Wireshark.
FAQ
Q: Why would I use Tcpdump over Wireshark?
A: Tcpdump is highly useful for environments where only command-line access is available, particularly on remote or headless machines.
Q: Is Tcpdump difficult to use for beginners?
A: While Tcpdump can initially seem daunting due to its command-line interface, familiarity comes with practice. Referring to documentation and tutorials can help ease the learning curve.
Q: Can I use the captured file from Tcpdump directly in Wireshark?
A: Yes, you can transfer the capture file to another system with Wireshark installed and analyze it there.
