In this comprehensive guide, we will explore how to create reusable modules in Terraform. Utilizing modules allows us to eliminate code duplication, thus facilitating the creation of resources of the same type multiple times without redundant copy-pasting. These modules can be effectively reused across different environments such as staging and production, maintaining a single source of code.
For illustration, we will construct a module for creating an S3 Bucket and demonstrate its versatility.
Prerequisites
- Basic understanding of Terraform.
- Terraform installed on your system.
- An active AWS Account (Sign up here if you don’t have one).
- AWS IAM User with ‘access_key’ & ‘secret_key’. (Ensure secure practices as outlined here).
Objective
- Create a custom Terraform module.
- Deploy an S3 bucket using the Terraform Module.
- Remove the created resource using Terraform Module.
Crafting a Custom Terraform Module
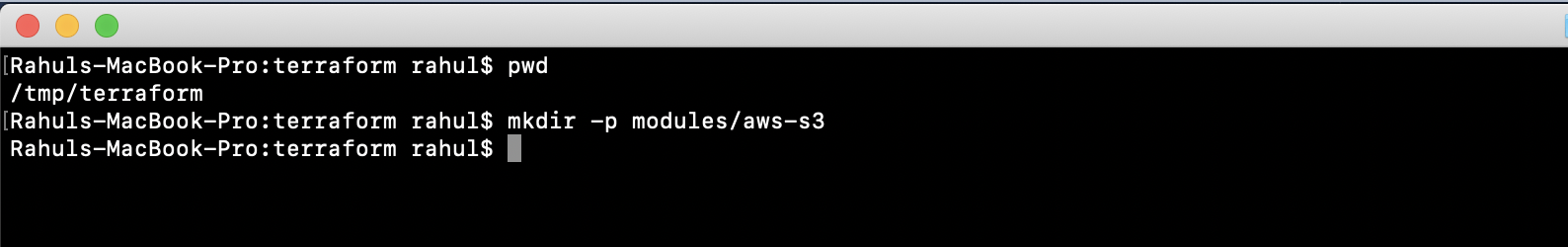
Initiate by making a directory for your Terraform “main.tf” file and the module:
mkdir -p modules/aws-s3
Next, create a “main.tf” file under modules/aws-s3. Insert the following code to establish a module for an S3 Bucket:
vim modules/aws-s3/main.tf
resource "aws_s3_bucket" "s3_bucket" {
bucket = var.bucket_name
acl = "public-read"
policy = <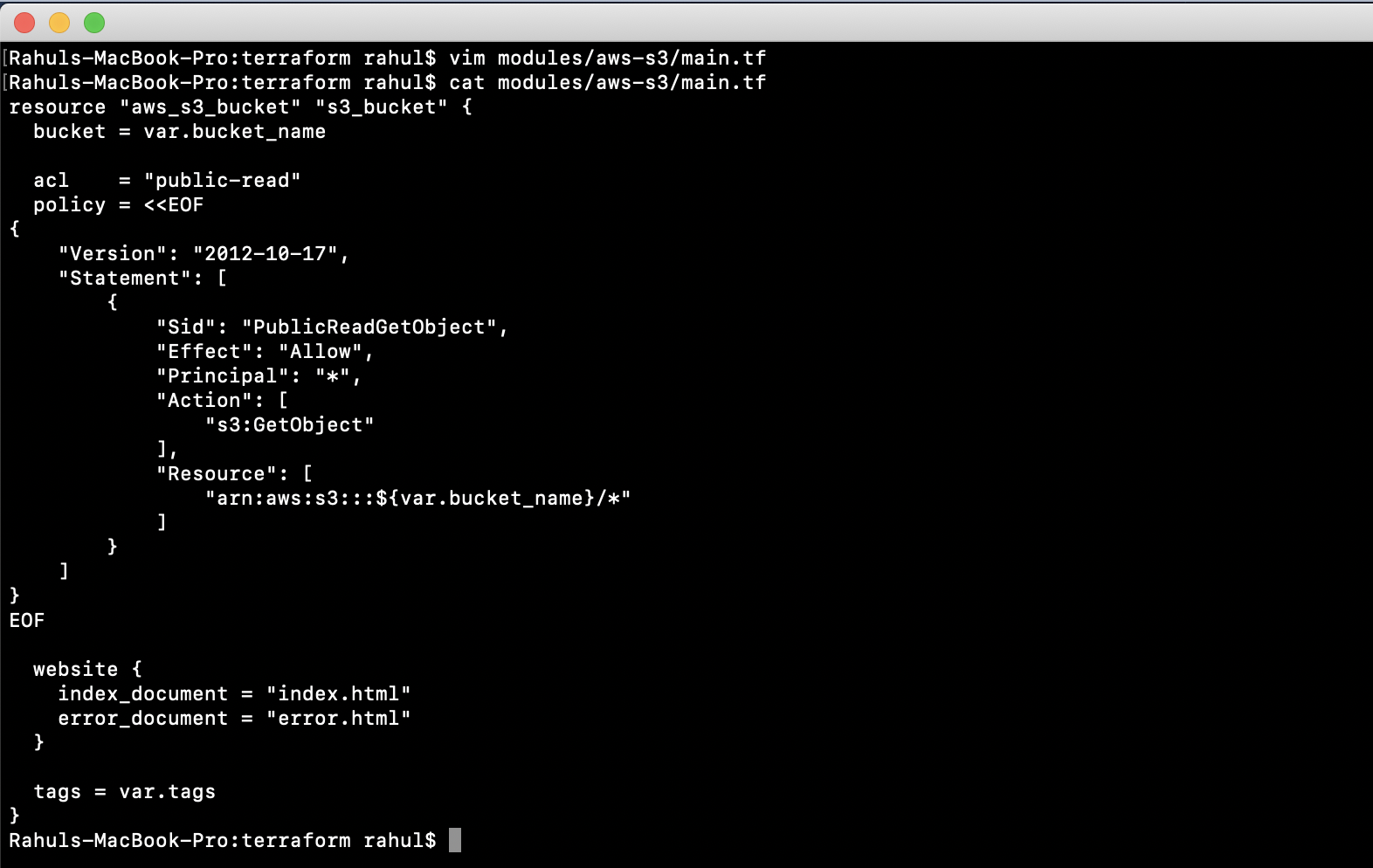
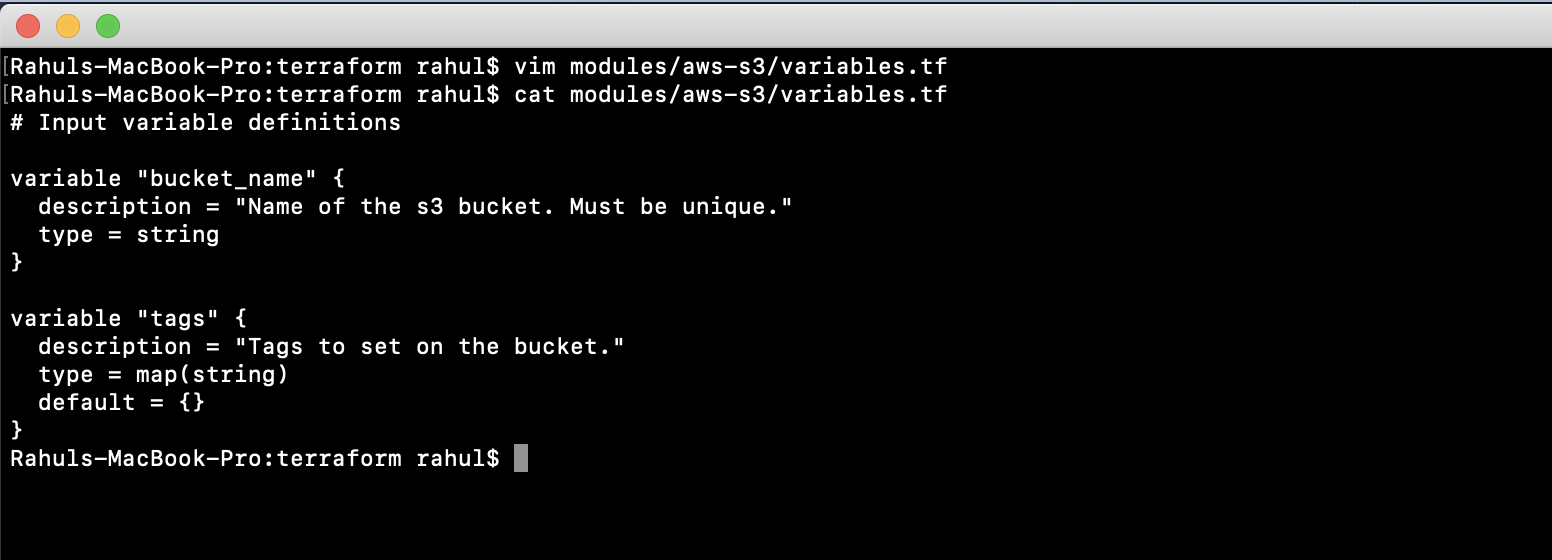
Declare the necessary variables in “modules/aws-s3/variables.tf”. You can optionally assign default values:
vim modules/aws-s3/variables.tf
variable "bucket_name" {
description = "Name of the s3 bucket. Must be unique."
type = string
}
variable "tags" {
description = "Tags to set on the bucket."
type = map(string)
default = {}
}
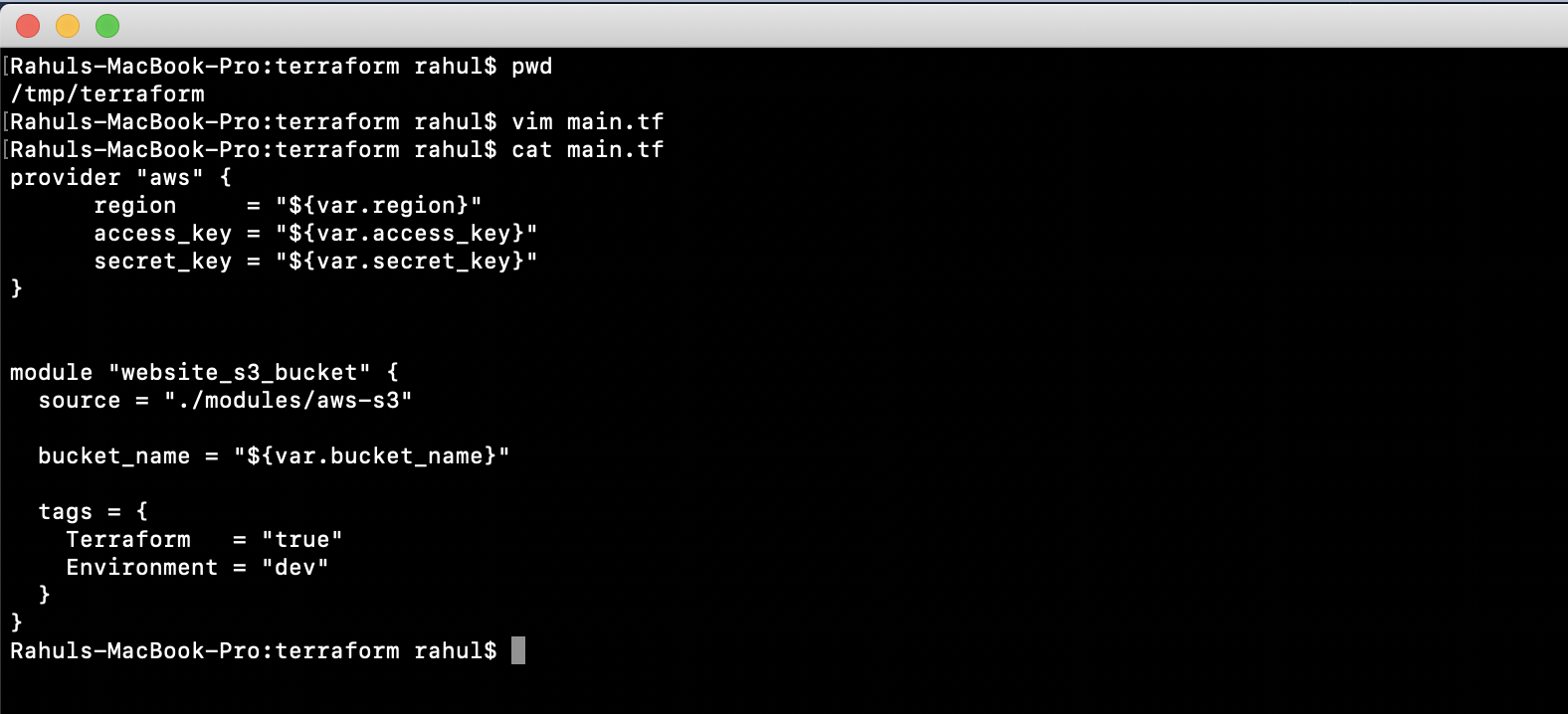
Now create a “main.tf” file to call the module we created. This involves including the module’s contents with specified values:
vim main.tf
provider "aws" {
region = "${var.region}"
access_key = "${var.access_key}"
secret_key = "${var.secret_key}"
}
module "website_s3_bucket" {
source = "./modules/aws-s3"
bucket_name = "${var.bucket_name}"
tags = {
Terraform = "true"
Environment = "dev"
}
}
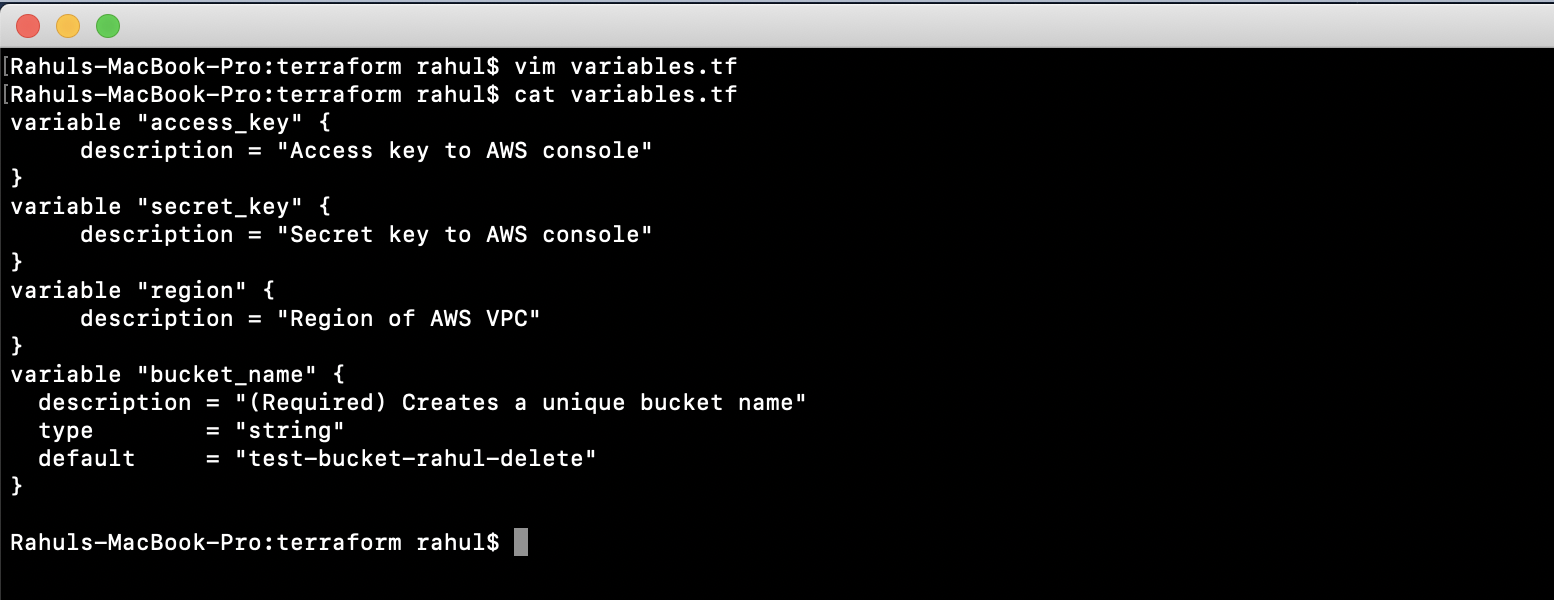
Define “variables.tf” to specify variables and assign default values for our module:
vim variables.tf
variable "access_key" {
description = "Access key to AWS console"
}
variable "secret_key" {
description = "Secret key to AWS console"
}
variable "region" {
description = "Region of AWS VPC"
}
variable "bucket_name" {
description = "(Required) Creates a unique bucket name"
type = "string"
default = "test-bucket-rahul-delete"
}
Next, include your AWS User Credentials in “terraform.tfvars” and ensure these keys remain confidential:
vim terraform.tfvars
region = "eu-west-3"
access_key = "YOUR_ACCESS_KEY"
secret_key = "YOUR_SECRET_KEY"
Deploying an S3 Bucket Using the Terraform Module
Ensure that your AWS credentials are correctly configured. Begin by running ‘terraform init’ to install necessary plugins:
terraform init
Use ‘terraform plan’ to review the impending changes to your infrastructure:
terraform plan
Execute ‘terraform apply’ to instantiate the resources on AWS. Confirm action upon prompt:
terraform apply
Following successful execution, verify the creation of your S3 bucket in the AWS console.
Removing the Created S3 Bucket Using Terraform
If the resource is no longer necessary, execute “terraform destroy” to remove it, effectively deleting the S3 bucket:
terraform destroy
Conclusion
This guide provided a step-by-step approach to writing a custom module and deploying an S3 bucket using Terraform. This reusable module exemplifies how to efficiently manage multiple S3 buckets by modifying variable values accordingly.
FAQ
Q: Can I create multiple instances of a resource using the same module?
A: Yes, by using different values for the module’s input variables, you can instantiate multiple resources with a single module.
Q: What should I do if I encounter an error during ‘terraform apply’?
A: Check to ensure that your Terraform configuration files are error-free and that your AWS access credentials are correctly set up. It is also helpful to review Terraform’s error messages for detailed troubleshooting.
Q: How do I secure my credentials in ‘terraform.tfvars’?
A: Store ‘terraform.tfvars’ securely and consider using environment variables or a credential management system to handle sensitive data.