Tripwire is a free and open-source Linux Intrusion Detection System (IDS) that monitors and reports unauthorized changes in files and directories on Linux systems. It provides alerts via email when modifications are detected, ensuring that your system remains secure. Tripwire achieves this by comparing the current filesystem state with a known baseline state and reporting any discrepancies.
Prerequisites
- A server running Debian 10.
- A root password configured on the server.
Getting Started
Begin by updating the system packages to the latest version with the following command:
apt-get update -y
With all packages updated, you can now proceed to install Tripwire.
Install Tripwire
Tripwire is available in the Debian 10 default repository. Install it using:
apt-get install tripwire -y
During installation, you will be prompted to configure email settings:
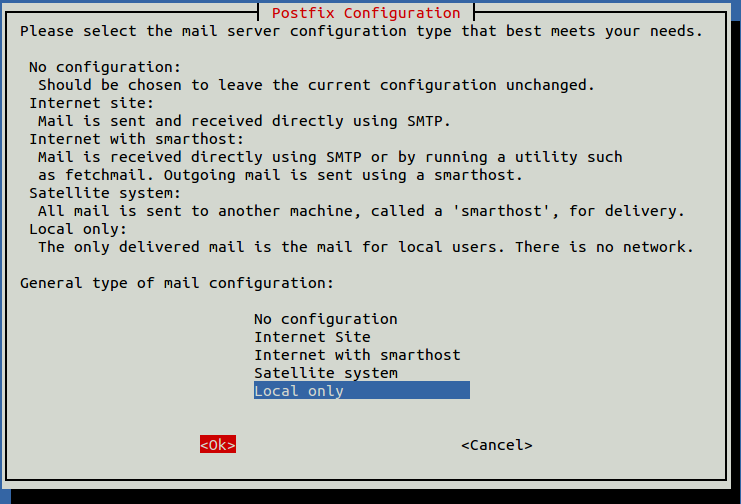
Select your preferred option and press ENTER. Next, configure your system mail name:
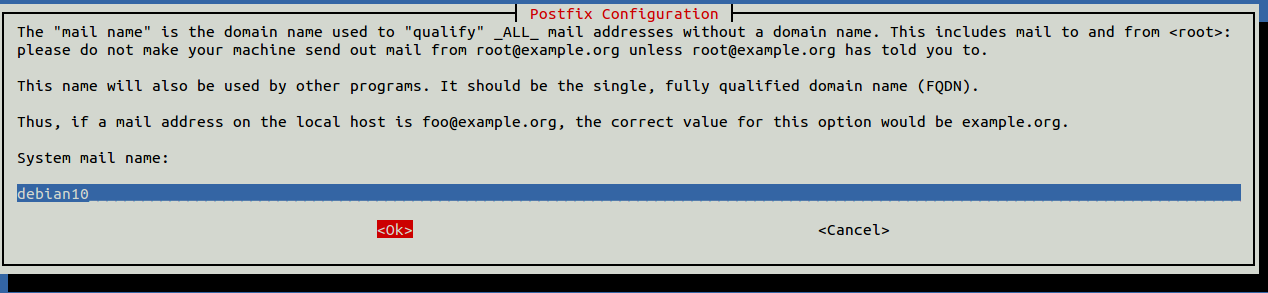
Enter your mail name and hit ENTER. You will then create your site key passphrase:
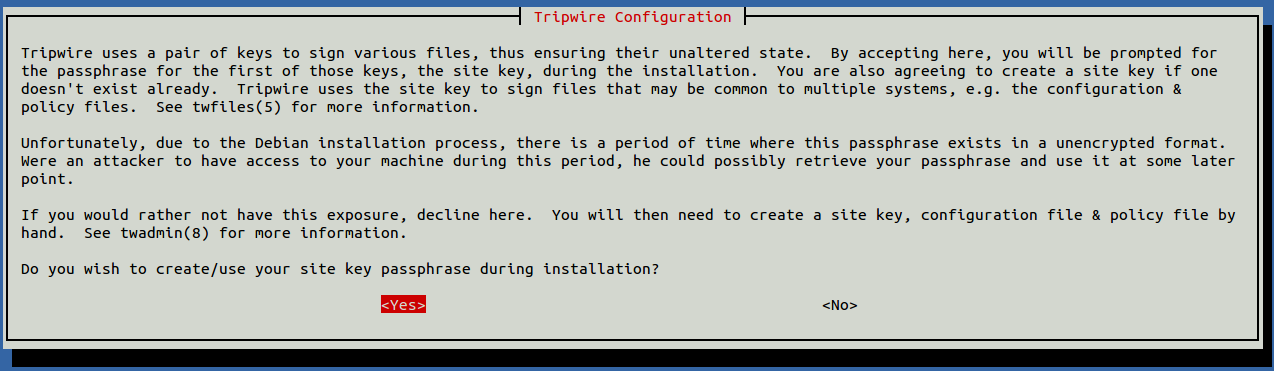
Choose Yes and press ENTER. Next, rebuild the Tripwire configuration file:
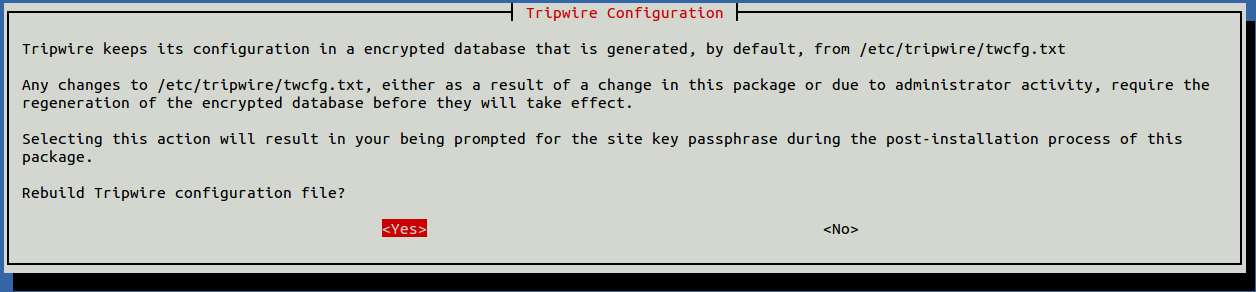
Select Yes to rebuild your Tripwire policy file:
Enter your site-key passphrase:
Finally, set your local key passphrase:
Tripwire is now installed. Complete the installation by clicking Ok on the final screen:
Configure Tripwire
Generate Tripwire keys and initialize the database by navigating to the Tripwire directory and listing all keys and files:
cd /etc/tripwire/ ls
You should see output similar to:
debian10-local.key site.key tw.cfg twcfg.txt tw.pol twpol.txt
Edit the Tripwire configuration by setting REPORTLEVEL to 4:
nano /etc/tripwire/twcfg.txt
REPORTLEVEL =4
Save your changes. Generate a new configuration file as follows:
twadmin -m F -c tw.cfg -S site.key twcfg.txt
Enter your site passphrase when prompted:
Please enter your site passphrase: Wrote configuration file: /etc/tripwire/tw.cfg
Next, create a Perl script, twpolmake.pl, to optimize the Tripwire policy:
nano twpolmake.pl
#!/usr/bin/perl
$POLFILE=$ARGV[0];
open(POL,"$POLFILE") or die "open error: $POLFILE" ;
my($myhost,$thost) ;
my($sharp,$tpath,$cond) ;
my($INRULE) = 0 ;
while () {
chomp;
if (($thost) = /^HOSTNAME\s*=\s*(.*)\s*;/) {
$myhost = `hostname` ; chomp($myhost) ;
if ($thost ne $myhost) {
$_="HOSTNAME=\"$myhost\";" ;
}
}
elsif ( /^{/ ) {
$INRULE=1 ;
}
elsif ( /^}/ ) {
$INRULE=0 ;
}
elsif ($INRULE == 1 and ($sharp,$tpath,$cond) = /^(\s*\#?\s*)(\/\S+)\b(\s+->\s+.+)$/) {
$ret = ($sharp =~ s/\#//g) ;
if ($tpath eq '/sbin/e2fsadm' ) {
$cond =~ s/;\s+(tune2fs.*)$/; \#$1/ ;
}
if (! -s $tpath) {
$_ = "$sharp#$tpath$cond" if ($ret == 0) ;
}
else {
$_ = "$sharp$tpath$cond" ;
}
}
print "$_\n" ;
}
close(POL) ;
Save and close the file. Generate a new configuration file:
perl twpolmake.pl twpol.txt > twpol.txt.new twadmin -m P -c tw.cfg -p tw.pol -S site.key twpol.txt.new
After entering your site passphrase, you’ll see:
Please enter your site passphrase: Wrote policy file: /etc/tripwire/tw.pol
Create a Tripwire database with:
tripwire -m i -s -c tw.cfg
You’ll see a warning if there are file system errors:
Please enter your local passphrase: ### Warning: File system error.
Display the database with:
twprint -m d -d /var/lib/tripwire/debian10.twd
To update the Tripwire database, use:
tripwire --update --accept-all
To test Tripwire, run:
tripwire -m c -s -c /etc/tripwire/tw.cfg
Verify Tripwire IDS
Create test files to ensure Tripwire detects them:
touch fil1 file2 file3 file4 file5
Run Tripwire to check for changes:
tripwire --check --interactive
Tripwire should list the new files in its report:
Open Source Tripwire(R) 2.4.3.7 Integrity Check Report
View reports later with:
twprint --print-report --twrfile /var/lib/tripwire/report/debian10-20210509-084636.twr
Automate Tripwire Reports
Set up a cron job for automatic Tripwire checks:
crontab -e
Add the cron schedule:
00 06 * * * /usr/sbin/tripwire --check
This will run Tripwire daily at 6:00 AM, with reports stored at /var/lib/tripwire/report/.
Conclusion
Congratulations! You have successfully installed and configured Tripwire IDS on Debian 10. This setup helps monitor and secure your system by detecting unauthorized changes in files or directories.
FAQ
What is Tripwire?
Tripwire is a Linux Intrusion Detection System that helps monitor and alert users about unauthorized changes in system files and directories.
Why should I use Tripwire?
Using Tripwire enhances your system’s security by identifying unauthorized changes that could indicate a security breach, allowing for timely responses to potential threats.
Can Tripwire send email alerts?
Yes, Tripwire can be configured to send email alerts when it detects changes, ensuring prompt notification of potential issues.
Is there a graphical interface for Tripwire?
No, Tripwire operates as a command-line tool, but it’s powerful and flexible with various customization options through configuration files.
How can I automate Tripwire checks?
You can automate Tripwire checks using cron jobs, allowing you to schedule regular integrity checks and receive reports on system changes.
