Jenkins is a powerful open-source automation tool designed for Continuous Integration/Continuous Delivery (CI/CD). Written entirely in Java, it boasts support for over 1000 plugins that aid in building, deploying, and automating projects. Jenkins has become a leading tool in accelerating development processes through automation and integrates various lifecycle processes such as building, documenting, testing, packaging, staging, deploying, performing static analysis, and more.
The tool supports multiple version control systems, including Git, Subversion, Mercurial, CVS, Perforce, and RTC. It can execute Apache Ant, Apache Maven, shell scripts, and Windows batch commands, making it highly versatile. With extensive community support, documentation, and a comprehensive wiki, Jenkins is among the most popular CI/CD automation tools. It offers flexibility through numerous tools, languages, and automation tasks, making development and deployment processes seamless.
This tutorial guides you through installing and setting up Jenkins with an Apache/httpd reverse proxy on a server running Rocky Linux 9. You will also learn to secure Jenkins using SSL and firewalld. Finally, this guide will walk you through creating a simple Jenkins build.
Prerequisites
To successfully complete this tutorial, ensure that you meet the following prerequisites:
- A server running Rocky Linux 9.
- A non-root user account with sudo/root administrator privileges.
- A domain name pointing to the server’s IP address. This guide uses the domain ‘jenkins.howtoforge.local’.
- SELinux configured to ‘permissive’ mode.
Installing Java OpenJDK
Jenkins is primarily written in Java, making it essential to have Java OpenJDK installed. In this section, we’ll install Java OpenJDK 11. The default Rocky Linux repository includes several versions of Java OpenJDK, and both Java OpenJDK 11 and 17 are compatible. We’ll proceed with Java OpenJDK 11 for this example.
sudo dnf install java-11-openjdk
Confirm the installation by typing ‘y’ when prompted and pressing ENTER.
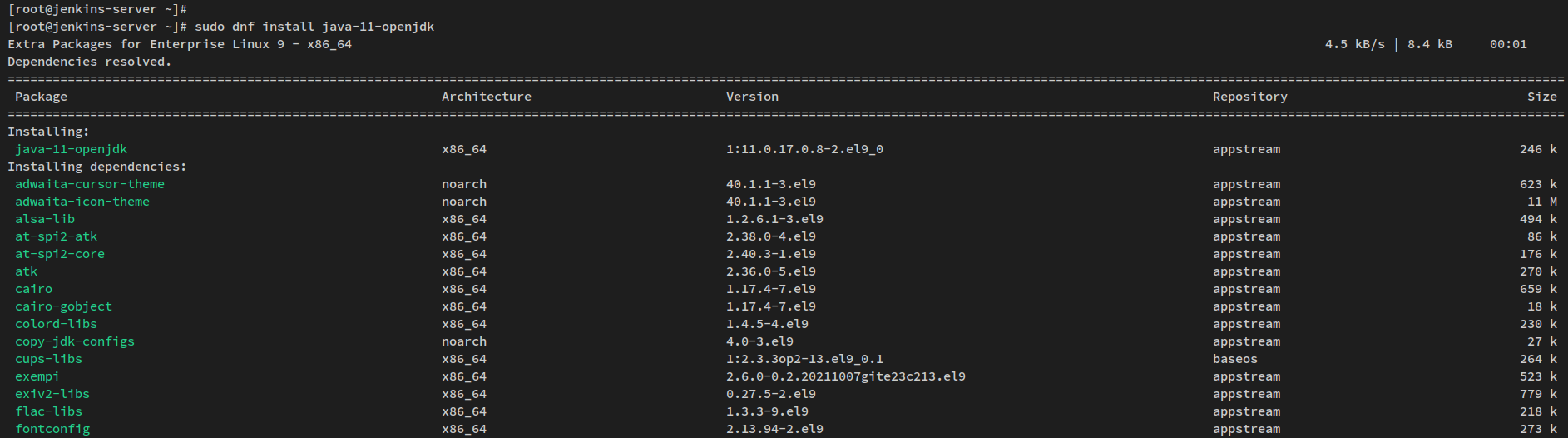
Once installed, verify the Java installation by running:
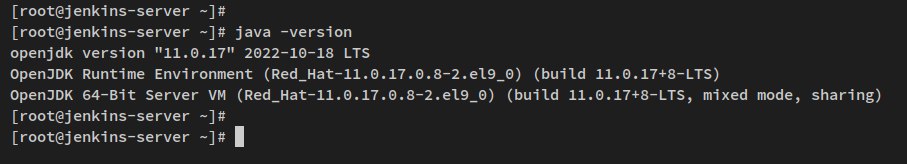
java -version
Adding Jenkins Repository
Jenkins can be deployed in various environments, such as virtual machines or using container technologies like Docker and Kubernetes. On Linux distributions, Jenkins can be installed via binary packages from the Jenkins repository.
Begin by installing necessary packages:
sudo dnf install wget curl
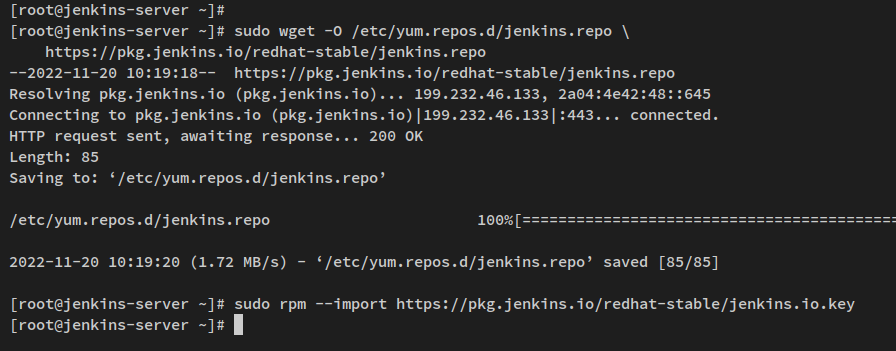
Download the Jenkins repository for RHEL-based systems using the command below. The repository will be saved at ‘/etc/yum.repos.d/jenkins.repo‘.
sudo wget -O /etc/yum.repos.d/jenkins.repo \ https://pkg.jenkins.io/redhat-stable/jenkins.repo
Afterward, import the GPG key for the Jenkins repository:
sudo rpm --import https://pkg.jenkins.io/redhat-stable/jenkins.io.key
Verify that the Jenkins repository is enabled by executing:
sudo dnf repolist

Installing Jenkins
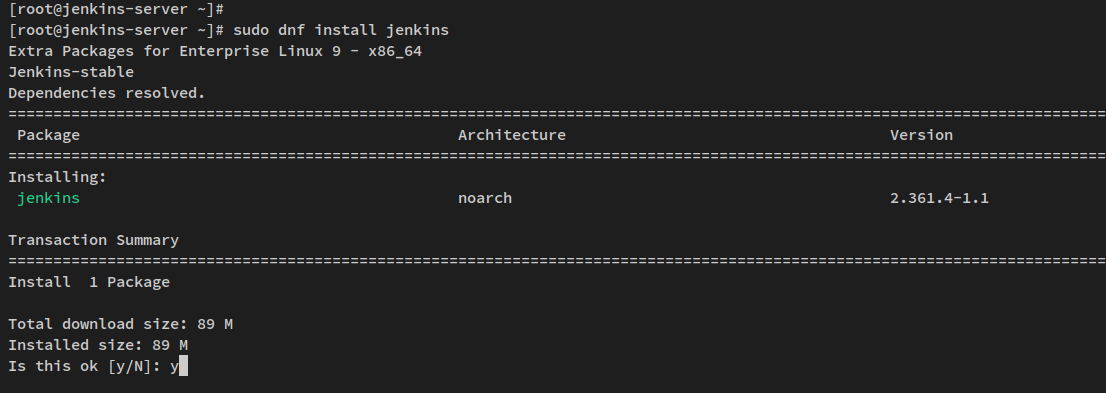
With the repository added, install Jenkins using the command below:
sudo dnf install jenkins
Confirm the installation with ‘y’ and press ENTER to proceed. You will install Jenkins version 2.361, the latest stable release at the time of this tutorial.
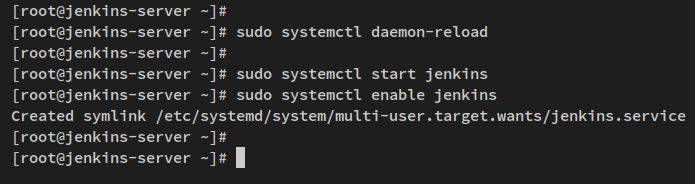
After installation, reload the systemd manager:
sudo systemctl daemon-reload
Then, start and enable the Jenkins service:
sudo systemctl start jenkins sudo systemctl enable jenkins
Verify the Jenkins service is active:
sudo systemctl status jenkins
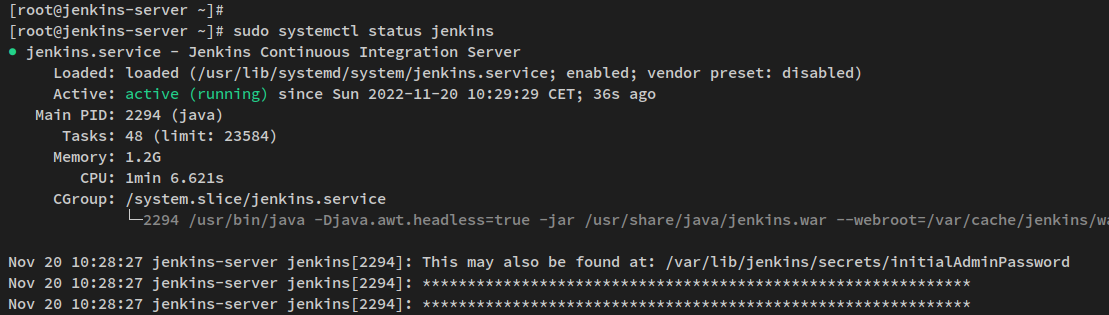
Jenkins is now running and ready for initial configuration with Apache/httpd as a reverse proxy.
Installing and Configuring httpd as a Reverse Proxy
Jenkins is accessible via TCP port 8080 by default. Installing and configuring Apache/httpd as a reverse proxy can provide a more user-friendly and secure interface.
Ensure you have a domain pointed to your server’s IP address and SSL certificates generated—either self-signed or via Let’s Encrypt.
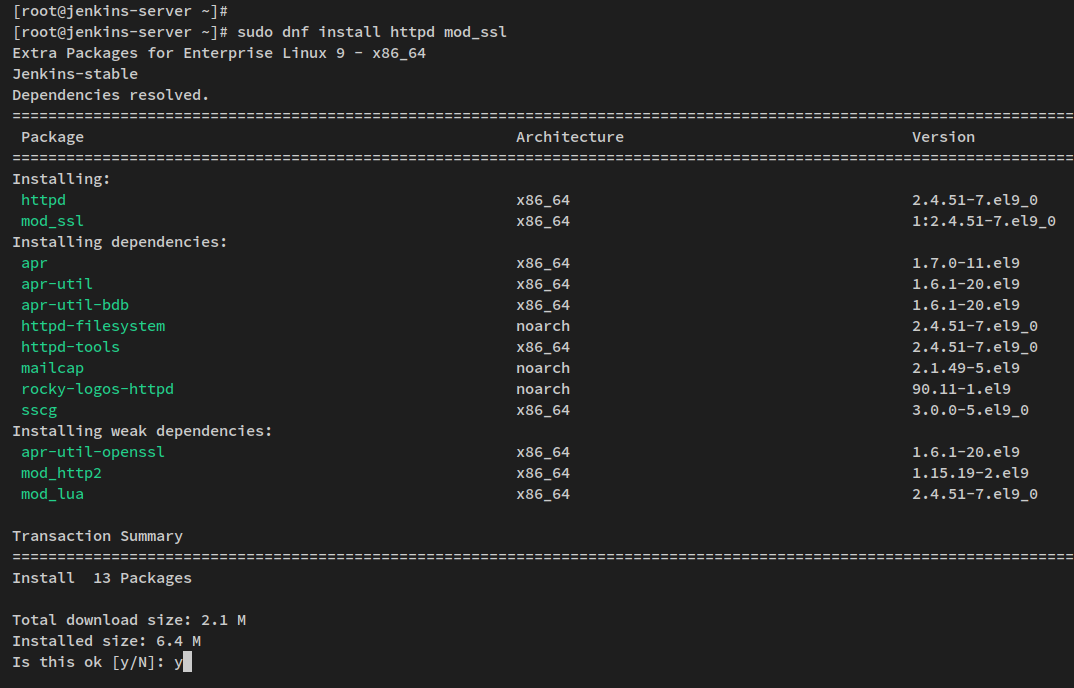
Start by installing the httpd web server and mod_ssl package:
sudo dnf install httpd mod_ssl
Generate a Self-signed SSL certificate for localhost:
openssl req -newkey rsa:2048 -nodes -keyout /etc/pki/tls/private/localhost.key -x509 -days 365 -out /etc/pki/tls/certs/localhost.crt
Create a new virtual host configuration file at ‘/etc/httpd/conf.d/jenkins.conf‘ and add the following:
<VirtualHost *:80> ServerAdmin webmaster@localhost Redirect permanent / https://jenkins.howtoforge.local/ </VirtualHost> <VirtualHost *:443> SSLEngine On SSLCertificateFile /etc/letsencrypt/live/jenkins.howtoforge.local/fullchain.pem SSLCertificateKeyFile /etc/letsencrypt/live/jenkins.howtoforge.local/privkey.pem ServerAdmin webmaster@localhost ProxyRequests Off ProxyPreserveHost On AllowEncodedSlashes NoDecode <Proxy *> Order deny,allow Allow from all </Proxy> ProxyPass / http://localhost:8080/ nocanon ProxyPassReverse / http://localhost:8080/ ProxyPassReverse / http://jenkins.howtoforge.local/ RequestHeader set X-Forwarded-Proto "https" RequestHeader set X-Forwarded-Port "443" </VirtualHost>
Save and close the file.
Verify the Apache configuration:
sudo apachectl configtest
Start and enable the Apache service:
sudo systemctl start httpd sudo systemctl enable httpd
Verify the service status:
sudo systemctl status httpd
Configuring Firewalld
Firewalld is the default firewall for RHEL-based systems, including Rocky Linux. It’s crucial to open HTTP and HTTPS services to allow Jenkins access.
Open these services with the following commands:
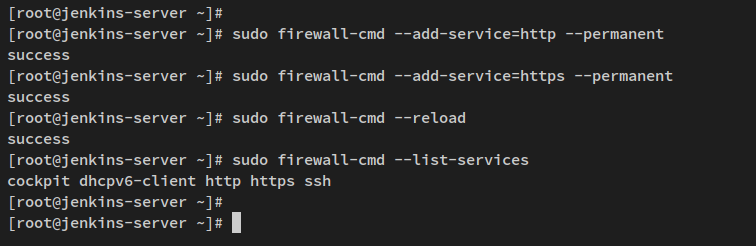
sudo firewall-cmd --add-service=http --permanent sudo firewall-cmd --add-service=https --permanent
Reload firewalld to apply changes and verify enabled services:
sudo firewall-cmd --reload sudo firewall-cmd --list-services
Jenkins Initial Configurations
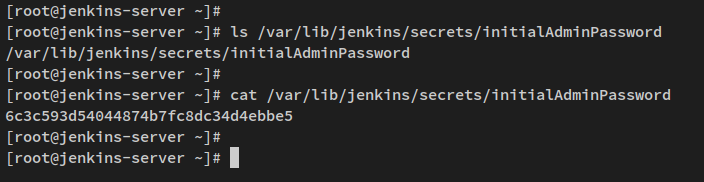
To start the Jenkins configuration, first obtain the initial password:
sudo cat /var/lib/jenkins/secrets/initialAdminPassword
Visit your Jenkins domain (e.g., https://jenkins.howtoforge.local/) in a browser. Enter the initial password and click ‘Continue‘.
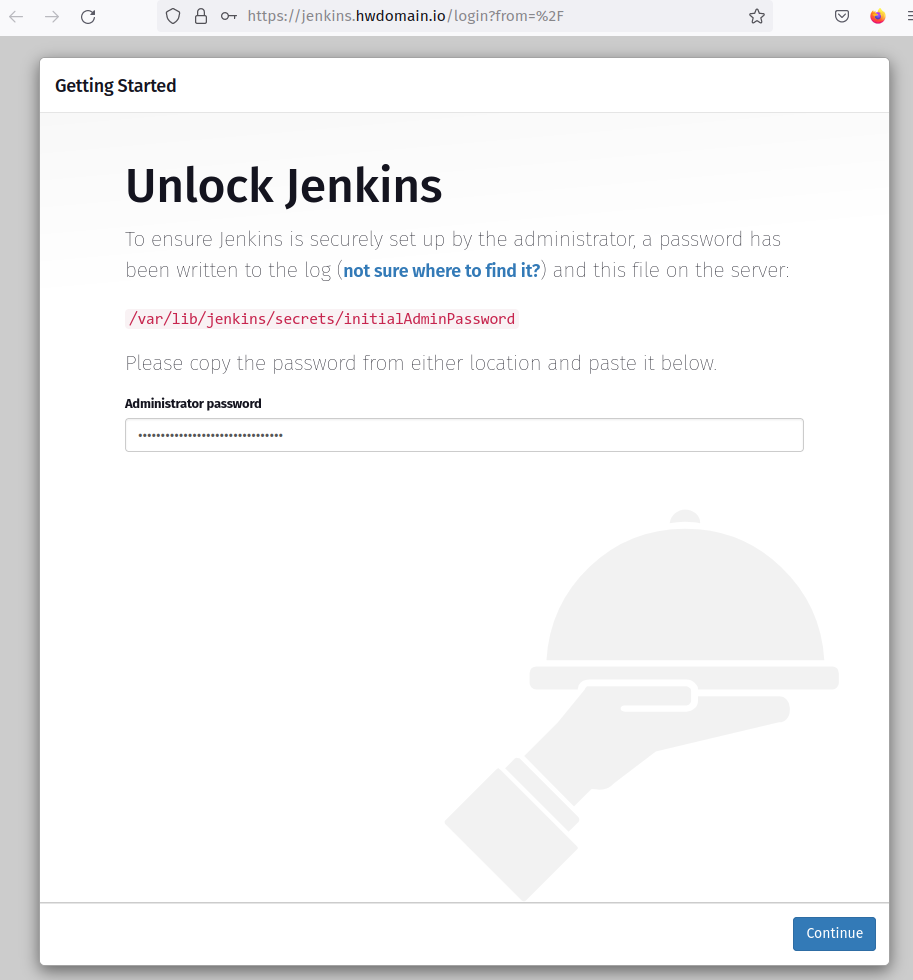
Select the option ‘install suggested plugins‘ to install recommended plugins or choose specific plugins manually.
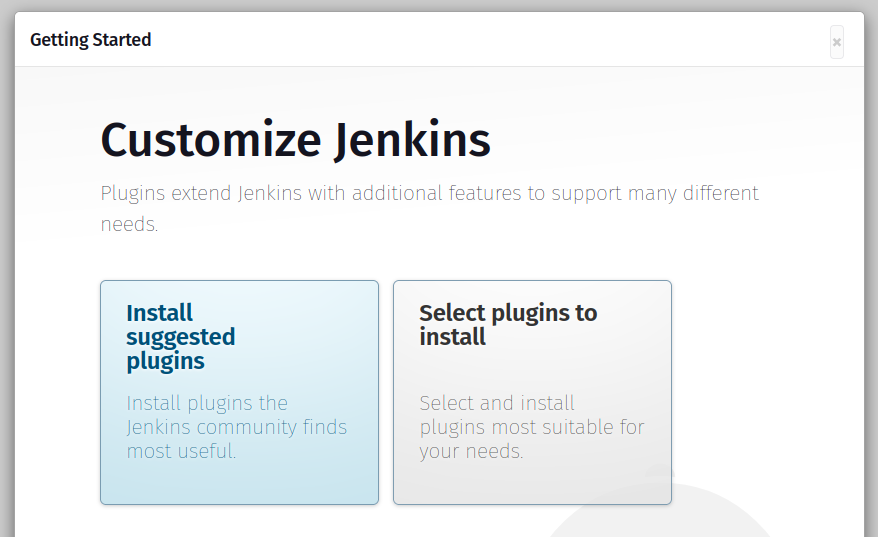
Upon plugin installation completion, create an administrator account and enter the necessary details.
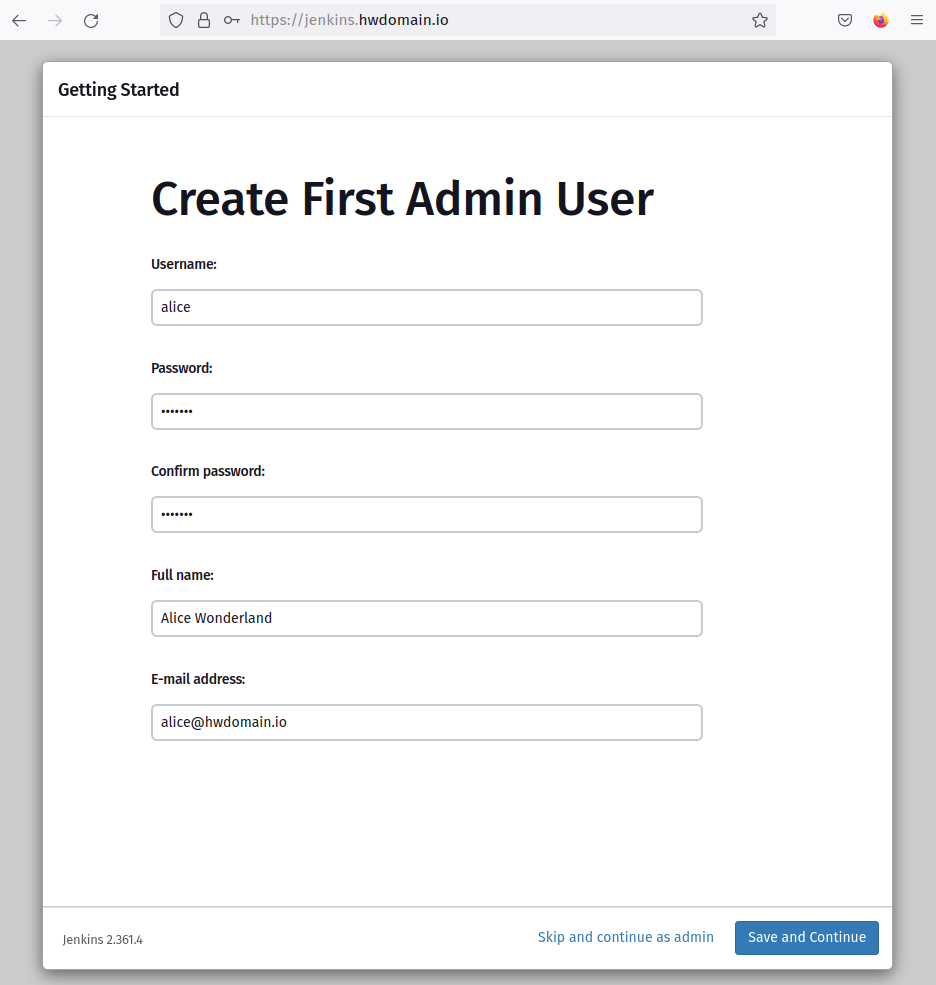
Input your Jenkins URL; here, it’s ‘https://jenkins.howtoforge.local/’ and click ‘Save and Finish‘.
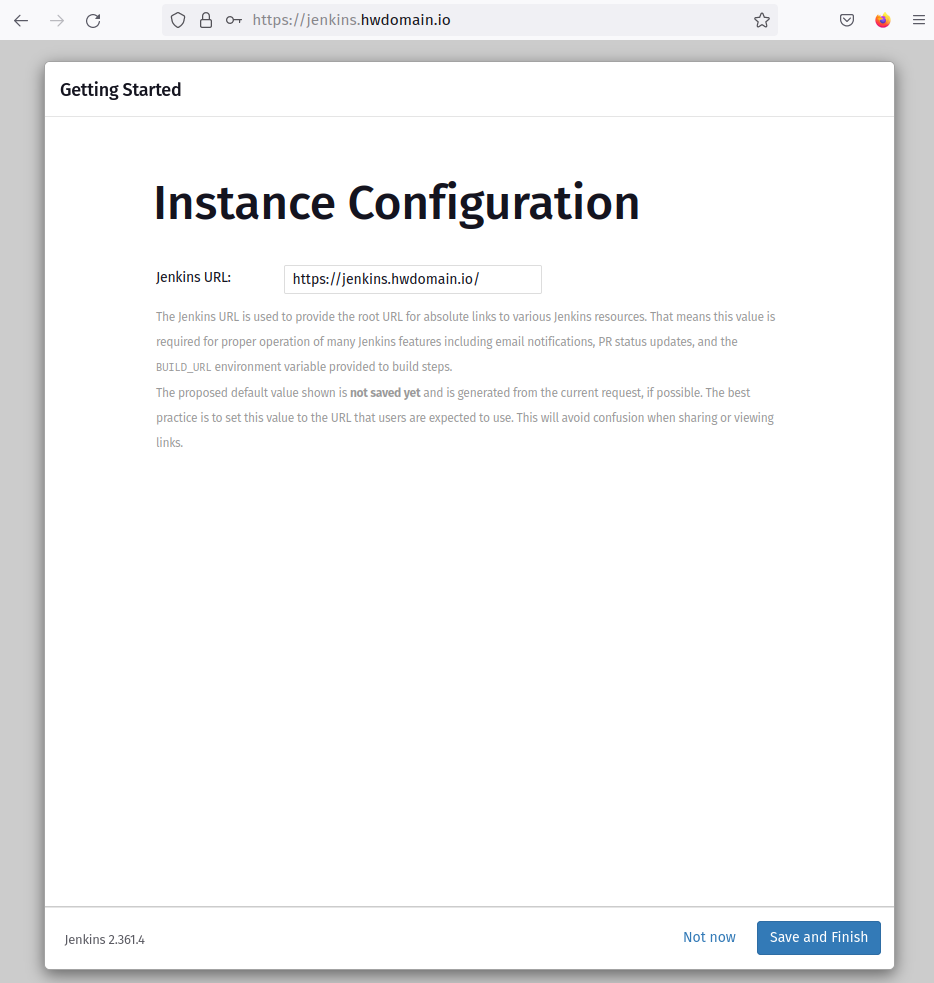
You’ll be redirected to the Jenkins dashboard, signifying successful initial setup.
Create First Jenkins Build
On the Jenkins dashboard, click ‘New Item‘ to create a new build.
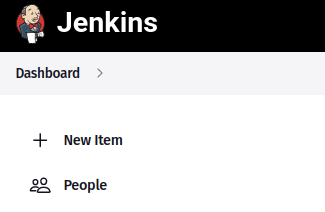
Specify the project name, selecting the “Freestyle project” type. Name your build “First Build“.
Click ‘OK‘ to proceed.
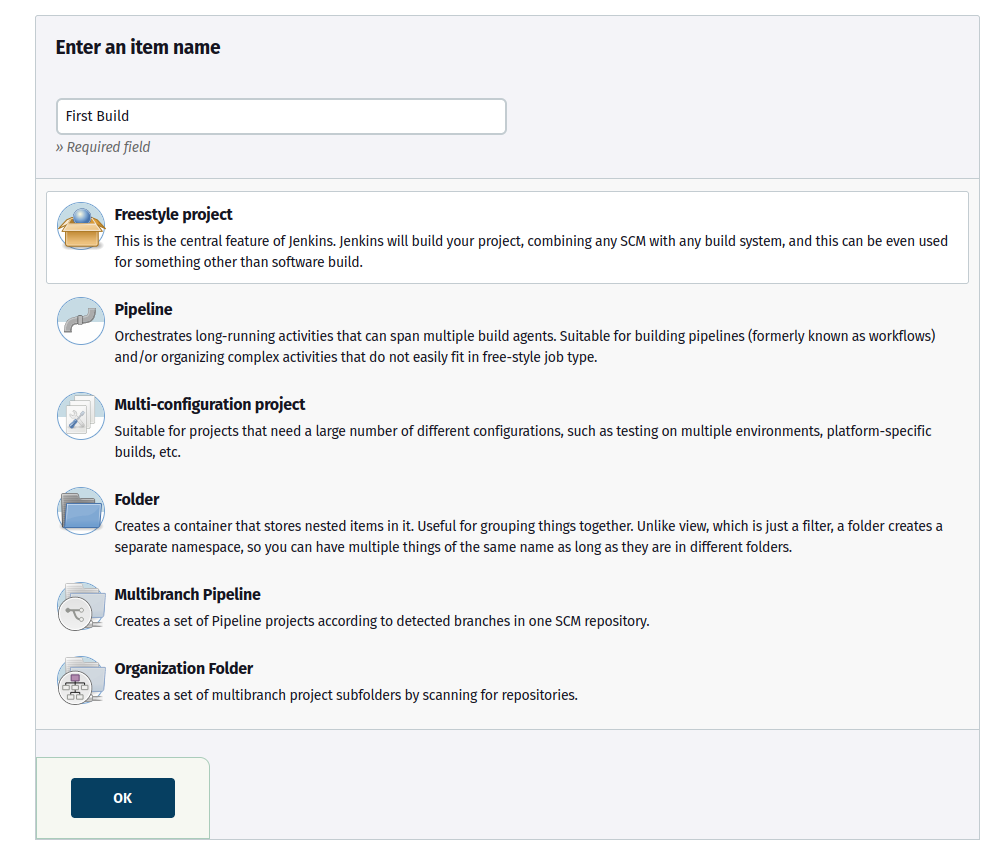
In the “Build Steps” section, choose “Execute shell” and enter:
echo "This is First build on jenkins"
Click ‘Save‘ to create your Jenkins build.
To execute the build, click ‘Build Now‘.
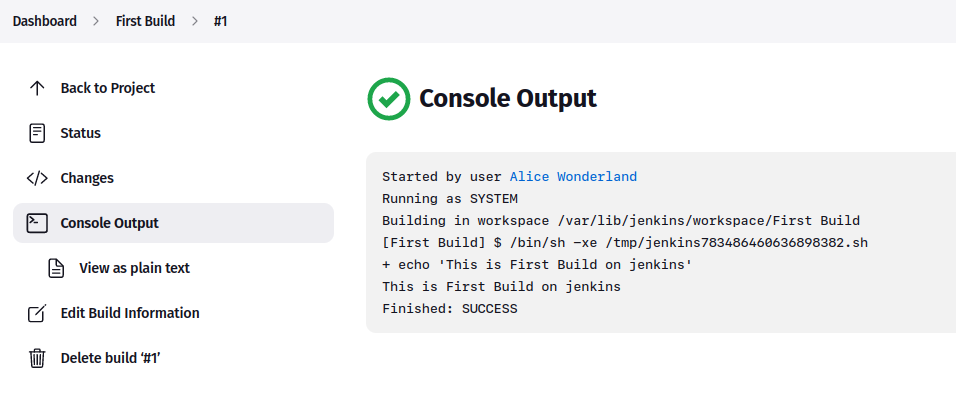
Review the build history by clicking the build number, then ‘Console Output‘ to view details.
Conclusion
In this tutorial, you’ve installed Jenkins on a Rocky Linux 9 server, configured Apache as a reverse proxy, and secured your Jenkins instance with SSL certificates and firewalld. Additionally, you’ve completed Jenkins’ initial setup and created a simple build.
Now that you’ve deployed Jenkins successfully, you can integrate your projects and set up builds for your applications. Jenkins’ functionality can be extended further with additional plugins to cater to your specific needs.
Frequently Asked Questions (FAQ)
Q: What is Jenkins?
A: Jenkins is an open-source automation server used for Continuous Integration and Continuous Delivery, helping to automate parts of software development related to building, testing, and deploying.
Q: Which operating system is this guide based on?
A: This guide is specifically for Rocky Linux 9, a popular Linux distribution.
Q: Why use Apache/httpd as a reverse proxy for Jenkins?
A: Using Apache/httpd as a reverse proxy enhances security, manages SSL certificates, and provides a better user interface via a custom domain.
Q: Can I use another version of Java for Jenkins?
A: Yes, Jenkins supports multiple Java versions. The example here uses Java OpenJDK 11, but you can also use Java OpenJDK 17.
Q: Are there other alternatives to securing Jenkins besides using SSL and firewalld?
A: Yes, other security measures include using network security groups, additional authentication plugins, and restricting access with OAuth2 or LDAP integrations.