LDAP (Lightweight Directory Access Protocol) is a widely-used open and standard application protocol for accessing and maintaining directory information services. Other applications, such as email clients, use LDAP to look up information from servers for authentication purposes.
OpenLDAP is an open-source implementation of LDAP developed by the OpenLDAP project. It is released under its own BSD-style license called the OpenLDAP Public License.
In this tutorial, we will guide you through the step-by-step installation of OpenLDAP on a Debian Buster 10 system.
Prerequisites
To follow this tutorial, ensure you have Debian 10 with at least 1GB of RAM, 25GB of free disk space, and 2 CPUs.
Steps to Install OpenLDAP
- Set Up FQDN
- Install OpenLDAP Packages
- Create Base User and Group
- Create a New User
- Basic LDAP Command
Step 1 – Set Up FQDN
Begin by setting up the FQDN (Fully Qualified Domain Name) of the OpenLDAP server. We’ll use ‘ldap.hakase.com’ as the FQDN for this installation.
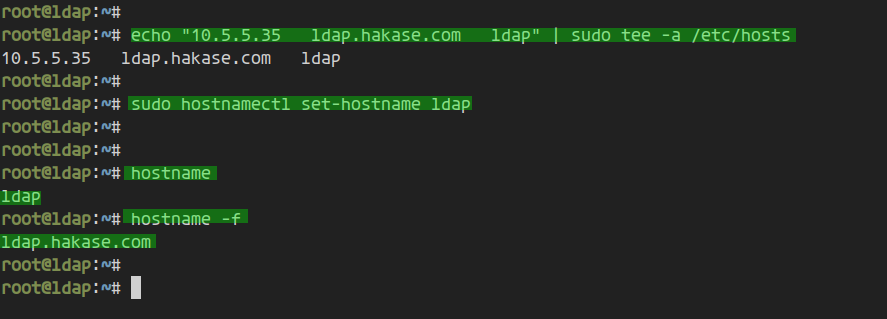
Modify the ‘/etc/hosts’ file using the following command:
echo "10.5.5.35 ldap.hakase.com ldap" | sudo tee -a /etc/hosts
Next, set the server’s hostname to ‘ldap’:
sudo hostnamectl set-hostname ldap
Log out and log back in, then verify the hostname and FQDN:
hostname hostname -f
This completes FQDN setup on Debian Buster 10.
Step 2 – Install OpenLDAP Packages
Install the OpenLDAP packages and set the LDAP admin password on your Debian system.
Use the following command to install ‘slapd’ and ‘ldap-utils’:
sudo apt install slapd ldap-utils
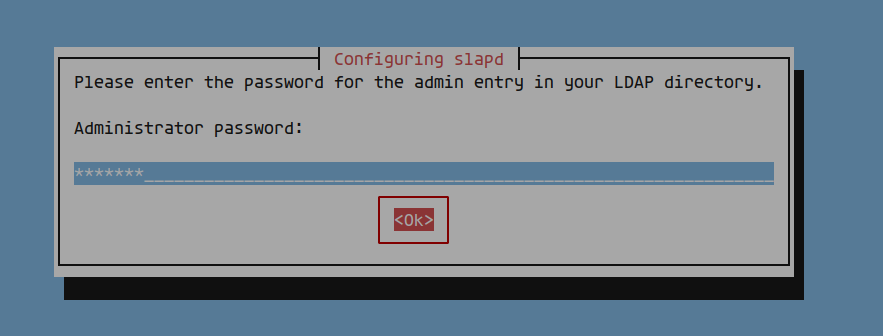
You will be prompted to enter the LDAP admin password—choose a strong one:
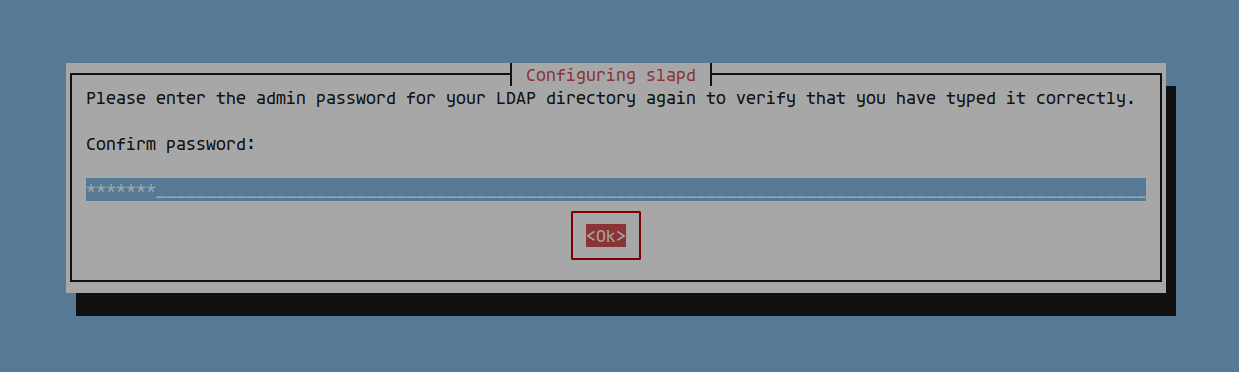
Re-enter the password to confirm:
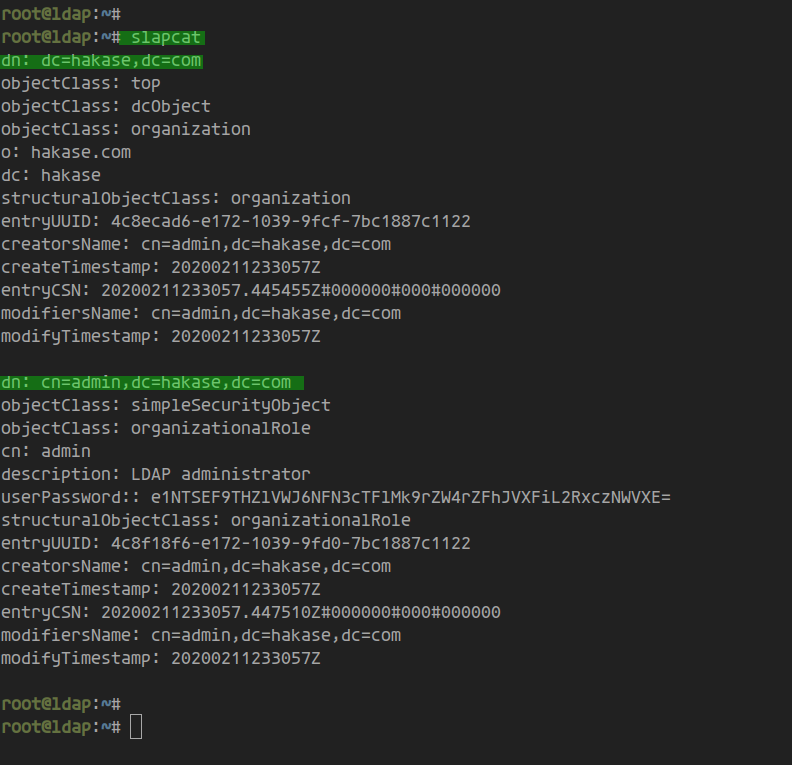
Once installed, verify the OpenLDAP setup using:
slapcat
Your system should display installation details with the server’s default FQDN:
For further verification, connect as an anonymous user:
ldapwhoami -H ldap:// -x
Step 3 – Create New Base User and Group
Create a base DN (Distinguished Name) for users and groups using LDIF (LDAP Data Interchange Format).
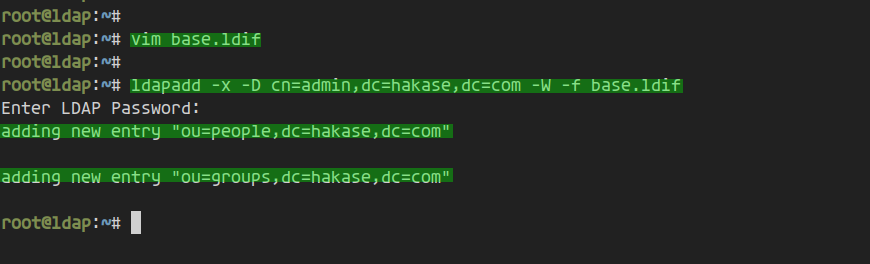
Create ‘base.ldif’ with vim:
vim base.ldif
Replace ‘dc=hakase,dc=com’ with your own domain details:
dn: ou=people,dc=hakase,dc=com objectClass: organizationalUnit ou: people
dn: ou=groups,dc=hakase,dc=com
objectClass: organizationalUnit
ou: groups
Save and close the file. Import the base user and group:
ldapadd -x -D cn=admin,dc=hakase,dc=com -W -f base.ldif
Enter your LDAP admin password and verify the result:
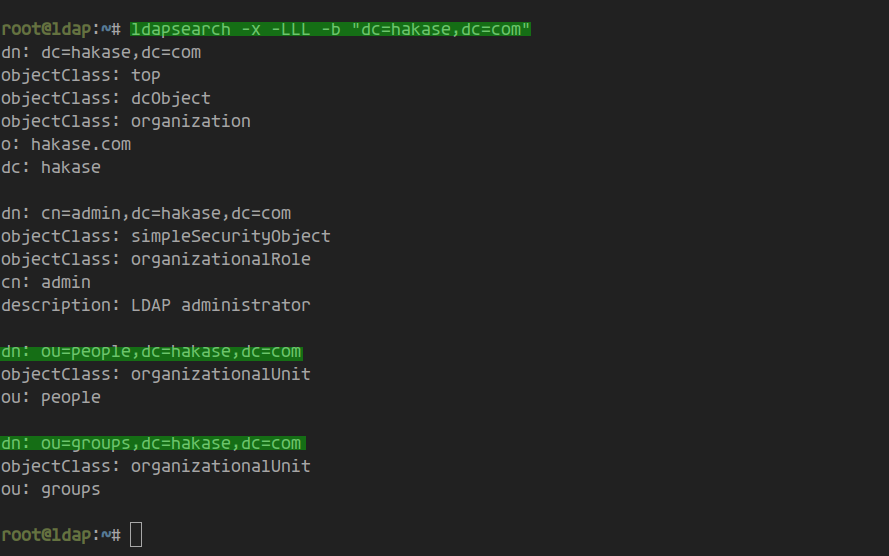
Verify the base user and group setup:
ldapsearch -x -LLL -b "dc=hakase,dc=com"
Output confirms the ‘people’ user and ‘groups’ group creation:
Step 4 – Create a New User
Now, create a new LDAP user:
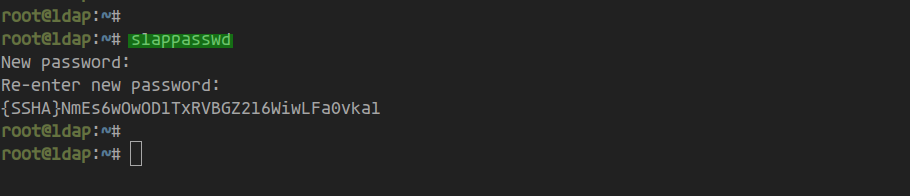
Generate an encrypted LDAP password:
slappasswd
Enter and re-enter a secure password to obtain its encrypted form:
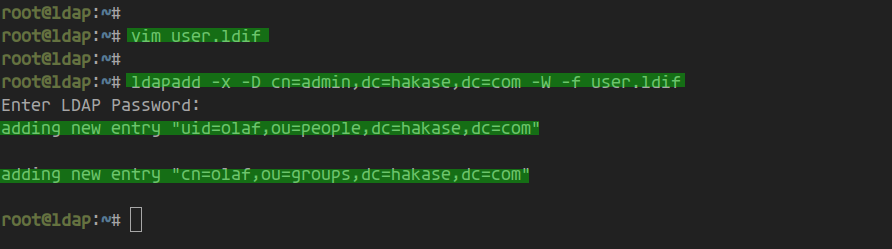
Create ‘user.ldif’ using vim:
vim user.ldif
Replace the username ‘olaf’ and password with your own details:
dn: uid=olaf,ou=people,dc=hakase,dc=com
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: shadowAccount
cn: olaf
sn: Olaf
userPassword: {SSHA}DX0BCCDmy7MzciI2vh6ymbywEmth6CQL
loginShell: /bin/bash
uidNumber: 2000
gidNumber: 2000
homeDirectory: /home/olaf
dn: cn=olaf,ou=groups,dc=hakase,dc=com
objectClass: posixGroup
cn: olaf
gidNumber: 2000
memberUid: olaf
Import the new user configuration:
ldapadd -x -D cn=admin,dc=hakase,dc=com -W -f user.ldif
Upon entering the LDAP admin password, the new user ‘olaf’ is confirmed as created:
Step 5 – Basic LDAP Commands
– Show All Objects on Base DN
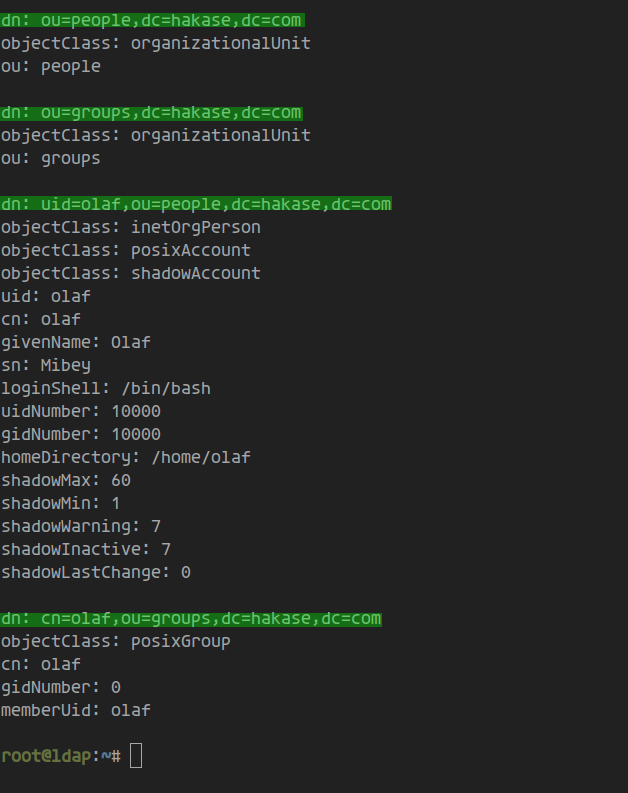
To list all objects on the base DN, use:
ldapsearch -x -LLL -b "dc=hakase,dc=com"
Results show all objects within your base DN:
– Change Password and Verify
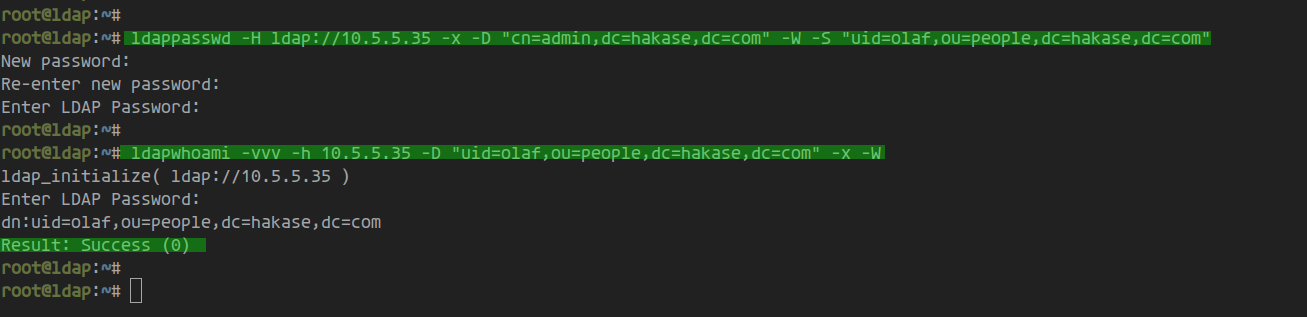
To change a user password, use ‘ldappasswd’ and adjust details as necessary:
ldappasswd -H ldap://10.5.5.35 -x -D "cn=admin,dc=hakase,dc=com" -W -S "uid=olaf,ou=people,dc=hakase,dc=com"
Confirm by checking the new password:
ldapwhoami -vvv -h 10.5.5.35 -D "uid=olaf,ou=people,dc=hakase,dc=com" -x -W
New password verification shows it works effectively:
– Delete a User
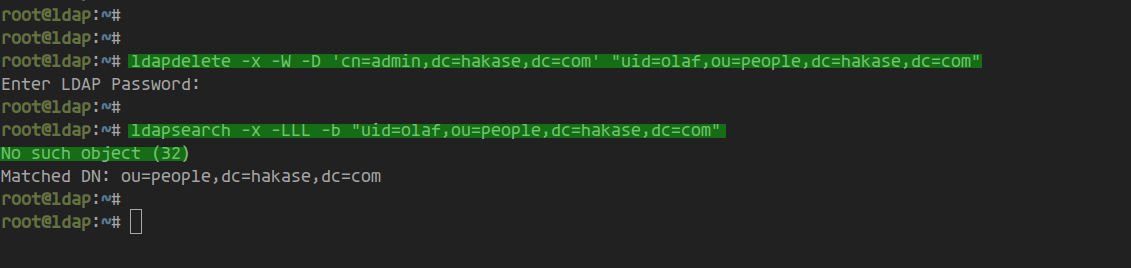
Remove a user with the ‘ldapdelete’ command:
ldapdelete -x -W -D 'cn=admin,dc=hakase,dc=com' "uid=olaf,ou=people,dc=hakase,dc=com"
Enter the LDAP admin password for successful deletion:
Congratulations! You’ve successfully completed the OpenLDAP installation on Debian Buster 10.
Useful Links
Frequently Asked Questions (FAQ)
- Q: What is OpenLDAP used for?A: OpenLDAP is used for directory services including user authentication and information lookup.
- Q: Is it possible to integrate OpenLDAP with other applications?A: Yes, OpenLDAP can be integrated with various applications, such as email clients and other software requiring user authentication.
- Q: How do I secure my OpenLDAP setup?A: Implement security measures such as enabling TLS/SSL for encrypted communication, configuring proper access controls, and regularly updating the software.