Linux is renowned for its robust security framework, acclaimed for both its performance and security features. While many assume that Linux is impervious to malware and viruses, it’s crucial to recognize that vulnerabilities do exist. Threats such as the “Bash” bug, Troj/SrvInjRk-A, and Linux/Rst-B specifically target Linux systems. Understanding the importance of Linux security, it’s wise to utilize tools for threat detection.
Lynis is a powerful tool designed to enhance Linux security. It is a free, open-source security scanner, available under the GPL license, supporting Linux and Unix-based systems like macOS, FreeBSD, NetBSD, and OpenBSD.
Lynis serves multiple purposes:
- Developers can secure their web applications.
- System administrators can identify vulnerabilities through health checks.
- Auditors can highlight areas that need additional security hardening.
- Penetration testers can discover critical security flaws that could lead to system compromise.
What will we cover?
This article covers the installation of Lynis and executing a system audit on Kali Linux.
How Lynis works
Lynis employs a modular scanning process, focusing only on detectable components. It doesn’t require additional dependencies for scanning. As more components are identified, the audit becomes more thorough. Upon initiating a Lynis audit, basic checks are conducted, followed by assessments of the operating system, tools, and software components. Lynis validates installed versions, runs enabled plugins and security tests, and compiles scan reports in files such as lynis.log and lynis-report.dat.
Installing and running Lynis on Kali Linux
To install Lynis using Kali’s package manager, execute:
$ sudo apt install lynis
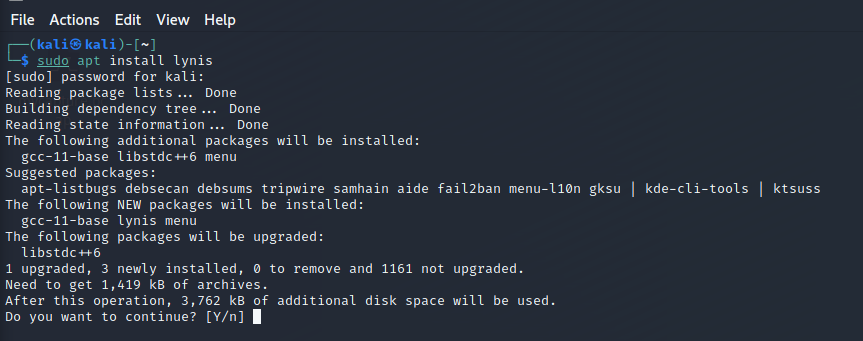
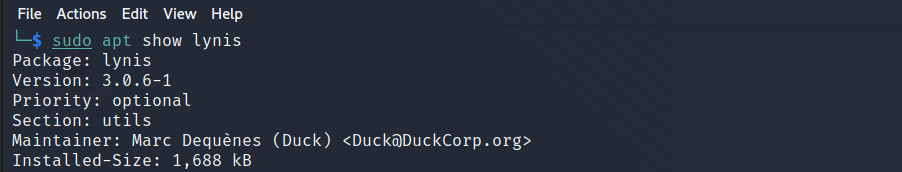
The currently installed version is 3.0.6-1, which may not be the latest. Check version details with:
$ sudo apt show lynis
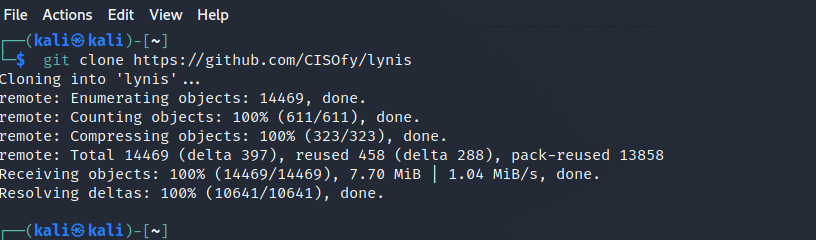
For the latest version, clone Lynis from its Git repository:
$ git clone https://github.com/CISOfy/lynis
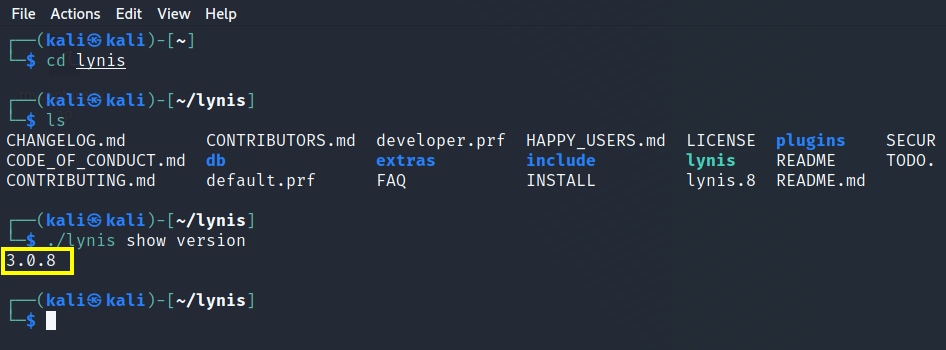
After cloning, navigate to the ‘lynis’ directory:
$ cd lynis
Verify the Lynis version:
$ ./lynis show version
Executing Lynis without Root
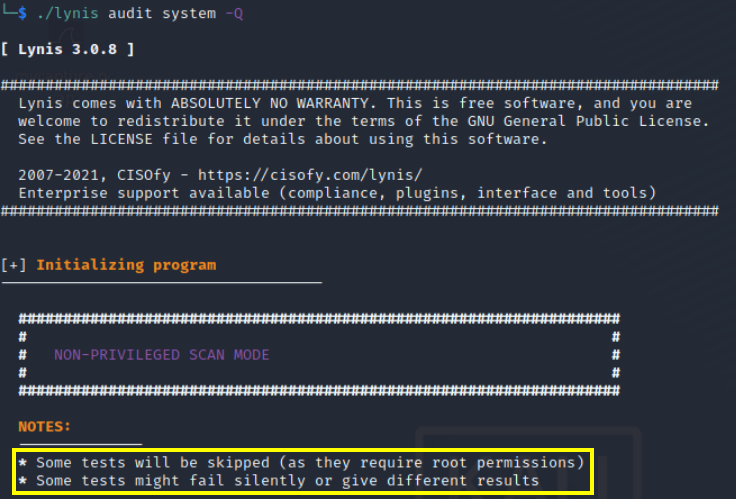
Lynis can be run in ‘NON-PRIVILEGED SCAN MODE’ without root access:
$ ./lynis audit system -Q
Some tests are unavailable in this mode due to lack of root permissions:
Executing Lynis with Root
Run Lynis with root privileges. You’ll encounter warnings on first execution:
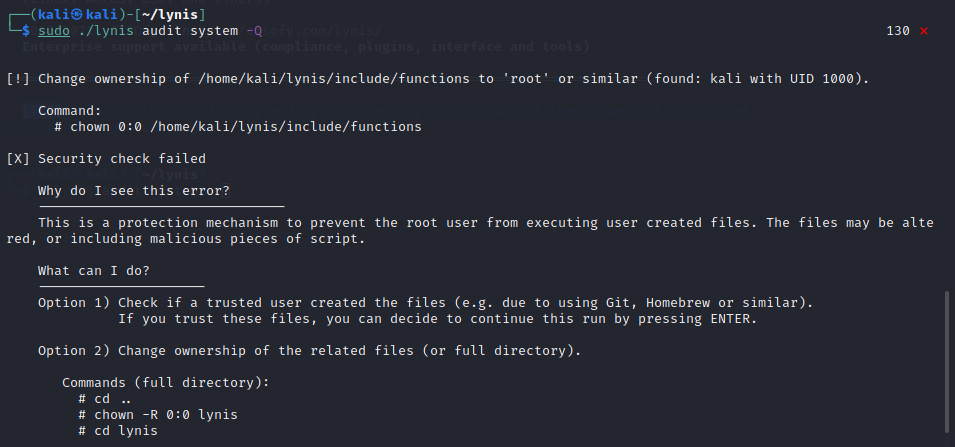
You can either proceed without modifications or adjust permissions:
$ sudo su cd .. chown -R 0:0 lynis cd lynis ./lynis audit system -Q
Running with root privileges allows more complete testing. Lynis categorizes scan results into warnings, suggestions, and detailed findings.
Lynis Commands
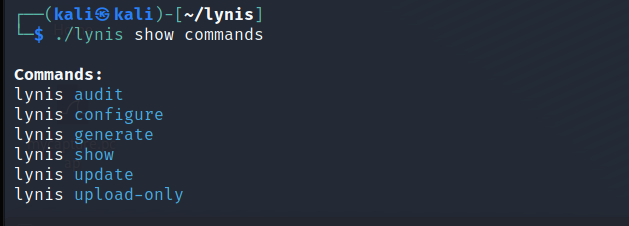
1. To view available Lynis commands:
$ ./lynis show commands
2. List available Lynis options:
$ ./lynis show help
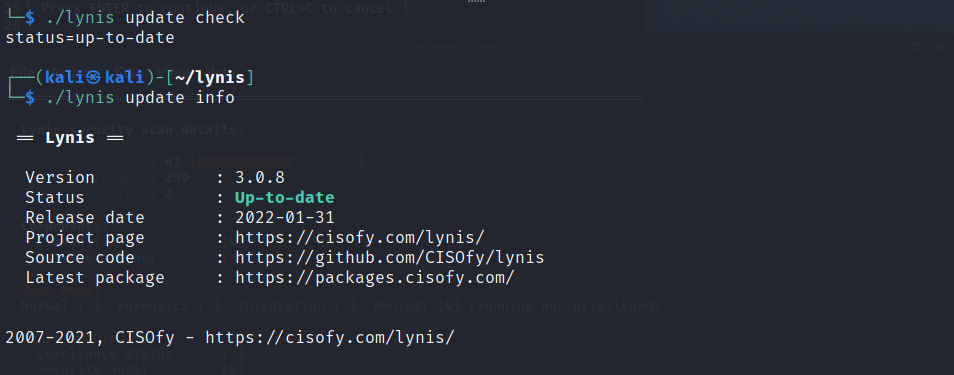
3. Check the installed version of Lynis:
$ ./lynis update check
$ ./lynis update info
4. View Lynis’s configuration profile:
$ lynis show profiles
To modify settings, view active settings with:
$ ./lynis show settings
Conclusion
This guide demonstrated installing Lynis on Kali Linux and conducting a system scan. For more advanced usage, consider auditing a remote system. Stay tuned for future guides covering these topics.
FAQ
What is Lynis?
Lynis is an open-source security tool used for auditing Linux and Unix-based operating systems. It identifies vulnerabilities and potential security improvements.
Is Lynis safe to use?
Yes, Lynis is a widely trusted and secure tool used by professionals globally for auditing system security.
Should I run Lynis as root?
Running Lynis as root provides a more comprehensive scan, although it’s possible to run it in non-privileged mode with limited tests.
Can Lynis be used on operating systems other than Linux?
Yes, Lynis supports Unix-based systems including macOS, FreeBSD, NetBSD, and OpenBSD, alongside Linux.
